01/2019 – Static vs. dynamic website - which one is the right for your company?
Static vs. dynamic website - which one is the right for your company?
Static or dynamic website? That's the basic question your company has to face when creating the own website. However, there is no general answer for better use, both solutions have their advantages and disadvantages, the input has to be weighed up from project to project.
On static websites, a HTML document is technically presented on the web server, which is written and designed like a kind of prospect.
Advantages
- No special technical requirements,
- requires no database connections,
- low and fast creation effort,
- cost-saving creation,
- low running costs,
- low memory capacity.
Disadvantages
- Usually, content can only be changed with the appropriate knowledge or software and requires a lot of time,
- the larger the pages, the more confusing the source code.
→ Target group: If you only plan a small website that has to be updated irregularly, a static website is sufficient – for example a simple web business card with address and opening hours.
Dynamic websites communicate with the server and are actively generated at the moment of their request.
Advantages
- Flexibility: Content can easily be expanded online without special knowledge and software,
- Individuality: Content and design can be changed independently,
- Multi-user operation: Multiple users are responsible for different parts of the website,
- easy design of multilingual websites,
- current content will be found by search engines.
Disadvantages
- Higher overhead, because servers and possibly database required,
- higher startup costs,
- higher running costs,
- larger storage space requirement.
→ Target group: Who plans a larger webiste, which should be maintained continuously with current content, such as search queries, ordering systems or form.
We would be happy to help you personally to find the ideal solution for your company.
After many successful years at our previous location, we decided it was time for a change. Due to our immense growth, we realised that we needed larger premises. Our new office offers more space for creativity, state-of-the-art technology and an environment that provides our employees with the best possible working conditions.
You can reach us at our new address from 27 January 2025:
aixzellent
c/o Theis Consult GmbH
Leonhardstraße 23-27
52064 Aachen
Our telephone numbers and e-mail addresses will remain unchanged, so you can reach us as usual.
We look forward to a fresh start in our new premises and a move that goes as smoothly as possible.

Two Factor Authentication
Again and again, millions of users are affected by security vulnerabilities. Two factor authentication can help to reduce the occurrence of identity theft, phishing attacks or other online scams. Because even if the password was cracked, hackers can be locked out and sensitive data is protected.
The proof of identity of the user is determined by a combination of two independent components, which must be used correctly. The three most common factors are usually specified as something that you know (Pin code) you have (bank card, physical key) and that you are (fingerprint, human voice). The combination does not necessarily have to consist of factors of different categories, but these must never be stored in the same place. Most often, one of the features is a physical token, while the other one is such as a security code, for example the combination bank card - PIN.
On secure computers it can be set to be asked for the code only the first time, for example at home on your PC or laptop. For sensitive accounts we recommend at least to establish the two factor authentication and thus to increase the protection of your data significantly.
Mobile Device Management with Relution - Device Management for schools and SME
The Corona Crisis has shifted workplaces and classrooms into the digital space. In the process, home offices and classrooms present new challenges for everyone. With Mobile Device Management Relution, Apple and Android devices can be managed remotely, regardless of manufacturer. In this way, devices purchased by the company or school authorities, or even private devices, can be used securely and conveniently in the company and school context. We have recently become official partners of Relution.
 The procurement of mobile devices raises the question of central administration for IT managers. Simple operation with a German-language interface and, in particular, compliance with data protection (DSGVO) are unavoidable criteria in the search for a suitable solution. The platform-independent Mobile Device Management Relution from the German software manufacturer M-Way Solutions meets these requirements. The two versions Fully Managed and Supervised enable full control over the remote management of devices. With the use of Workprofile or Bring Your Own Device (BYOD), private devices can also be used. This makes the software interesting for different application scenarios in schools and also for SMEs. The strict separation of private and work-related data is ensured by appropriate configurations. The multi-client capability of Relution makes it possible to provide separate areas for different fields of application. Managed devices can be configured so that only selected functions, apps and content are available to users and specific access rights are granted. By connecting to existing systems, user directories can be integrated for authentication and local shares for secure file storage.
The procurement of mobile devices raises the question of central administration for IT managers. Simple operation with a German-language interface and, in particular, compliance with data protection (DSGVO) are unavoidable criteria in the search for a suitable solution. The platform-independent Mobile Device Management Relution from the German software manufacturer M-Way Solutions meets these requirements. The two versions Fully Managed and Supervised enable full control over the remote management of devices. With the use of Workprofile or Bring Your Own Device (BYOD), private devices can also be used. This makes the software interesting for different application scenarios in schools and also for SMEs. The strict separation of private and work-related data is ensured by appropriate configurations. The multi-client capability of Relution makes it possible to provide separate areas for different fields of application. Managed devices can be configured so that only selected functions, apps and content are available to users and specific access rights are granted. By connecting to existing systems, user directories can be integrated for authentication and local shares for secure file storage.
The software does not store any data in a cloud, can be easily integrated into the existing IT infrastructure and operated locally. Relution scores well on the topic of data protection, and that is important: Not only does the GDPR classify the data of underage students as particularly worthy of protection, but data in the corporate context should also be well protected. In addition to the necessary professional and technical aspects, Relution also fulfills the legal aspects. As the software can be operated regionally as SaaS (Software-as-a-Service) as well as on the company's own infrastructure, the risk of data misuse is significantly reduced. Here, Relution itself takes a stand on the topic of digital sovereignty for education: https://relution.io/news/digital-sovereignty/
As a full-service provider, we help both school boards and companies with their own data protection. We develop individual concepts for different requirements. Simply contact us without obligation if you need further information.
Further information on e-learning in the field of education can also be found at https://www.aixzellent.com/en/premium_e-learning and for SMEs at https://www.aixzellent.com/en/premium_applicationhosting.
ownCloud: data security, control & flexibility with aixzellent
ownCloud is a free software to store data on (own) servers which are automatically synchronised with local registers by the use of a respective client-software. This allows for instance different persons (employees) to access and work on Microsoft Office documents, images, etc. Using the ownCloud App for Android and iOS allows additionally to manage and synchronise data via mobile devices. Unlike commercial cloud storage services, ownClowd may be installed on private servers or webspaces without any additional costs. The control over sensitive data stays with its owner who decides how, when and with whom he/she wants to share the data with, instead of leaving this control to a third party. Moreover, the use of ownCloud is not restricted to a particular operating system and allows for the integration of and combination with additional applications – like for instance groupware solutions, file manager, external storages, etc. – via a WebDAV interface connection. Thanks to its modular set-up, the software may be extended with several plug-ins introducing additional functions. We transfer your data exclusively via encrypted SSL/TLS connections. Thanks to its open source nature, ownCloud offers next to high data security and flexibility also a ligh level of transparency and the possibility to shape the software actively. We keep the software updated regularly which is additionally protected by an anti-virus program. Next to our new ownCloud service, we also offer managed hosting solutions for a Private Cloud based on Afresco Share/One and more general information on Private Clouds. We are happy to advise you personally in order to design your own individual solution based on your wishes and needs in close cooperation with you. Please feel free to contact us.
This is how aixVPN contributes to your safety anywhere & anytime!
In times of increasing digitalisation and an ever-increasing use of public WLAN networks, Virtual Private Networks (VPNs) offer a simple and highly secure solution to protect oneself against attacks on personal and/or business data at any time and from anywhere. This is both for private and business purposes more than only useful. Current risks make the renouncement to use this security-plus provided by VPN almost acting carelessly. Not until VPN connections are used, you will be able to access all services you need one hundred percent securely.
Next to the protection against attacks when using public, unsecured WLAN networks – firewalls, geoblocking and unwanted tracking can also be prevented by making use of your very own VPN tunnel. Not to mention the fact that governments in many parts of the world have been systematically monitoring users or even blocking certain Internet sites, thereby severely restricting and threatening the freedom of expression, and thus human rights.
The handling is moreover particularly simple and above all absolutely securely. After we have set up your VPN connection and provided you with your very own personal security certificate, your entire traffic is secured through your German VPN server so that your actual IP address is not visible to the visited websites and services.
Our aixVPN solution based on OpenVPN ensures high security through a SSL/TLS tunnel. Additionally, the type of the encryption algorithm and the key length play a decisive role. aixVPN has an AES-256 encryption, an RSA key length of 4096 bits, and a cryptographic SHA-2 hash function. These features go far beyond what is recommended by experts.
And best of all is that you do not have to worry about the installation, configuration and secure operation – we will take care of everything, from the set-up, to maintenance, to regular updates and protection! Curious? Let yourself be inspired by our aixVPN solutions for private applications (Starter) as well as for companies (Premium). If you have any questions or suggestions, please do not hesitate to contact us!
[Sources: https://www.privacytutor.de/vpn/ https://www.computerwoche.de/a/vpn-verbindungen-das-muessen-sie-wissen,3326654]
Home office at the time of corona pandemic
Since the end of 2019, the lung disease COVID-19 triggered by new coronavirus SARS-CoV-2 has been spreading rapidly, has reached Europe in the meanwhile and has quickly developed into a global pandemic. "Flatten the Curve" is now the order of the day: the spread of infections has to be slowed down as much as possible to prevent the health care system from collapsing. Now, more and more companies are preparing for home office. This is not just a tool to slow the spread, but in worst case the only way to keep the business going. Groupware functions and cloud services are fundamental for a functioning home office.
 Businesses can help keep the contagion curve flat. As a precautionary measure to prevent the virus from spreading, people are working exclusively in their home office for several weeks and reduce contact to other people to a minimum. Even the absence of work and the lack of direct contact between the workforces can slow down the spread of the corona pandemic.
Businesses can help keep the contagion curve flat. As a precautionary measure to prevent the virus from spreading, people are working exclusively in their home office for several weeks and reduce contact to other people to a minimum. Even the absence of work and the lack of direct contact between the workforces can slow down the spread of the corona pandemic.
The right equipment: Compared to a large monitor with keyboard, a laptop is not an equivalent work tool. Tips for setting up the workplace and aligning the desk and office chair can be found, for example, at https://media.t3n.de/redaktion/homeofficeguide/t3n_Homeoffice_Guide.pdf. There you will also find tips on digital offers for children and important hygiene advices for time at home.
The exchange of data should generally only be encrypted (TLS/SSL) and take place via a virtual private network (VPN), which is set up by the IT department. In order to be able to protect and exchange company-internal data securely, a VPN is necessary and must be provided with a safe operating concept, so that no hole is torn in company-internal IT security measures. In this way, employees can be provided with secure access to the company's internal network. If you want to exchange data quickly, easily and independently from end devices in another way, you will find an alternative with open source clouds. Since numerous public cloud storage services are not compatible with the GDPR, alternatives such as Nextcloud should be used:
→ https://www.aixzellent.com/de/premium_privateclouds.
The distance also changes the communication structures of the teams internally and externally. Messenger programs and the possibility of video conferencing are an important tool for collaboration in remote workplaces. There are also challenges here: The video connection may not work if employees live in an area that is not yet connected to fiber optics or the bandwidth for the private connection could not allow a bandwidth to be linked to professional requirements. For video conferencing, there should be a technical infrastructure with upload speeds of more than 10 Mbit/s if possible. Project management tools help planning projects and to-dos, given they are not already integrated as accompanying project structures anyway.
In general, the following applies to IT security issues: All tools used should be discussed and set up with the company's data protection officer. Scammers and other criminals are already trying to use the crisis. IT administrators who otherwise quickly take care of maintenance tasks personally in the office instead of explaining it to all employees must now find other ways of performing their tasks. For remote maintenance, we recommend solutions such as NoMachine or Teamviewer. With these tools employees can access someone else's computer and quickly provide help with IT questions and problems.
Another problem with home office: executives can no longer see their teams working and thus have doubts about their productivity – regardless of whether these doubts are justified or not. Only the results achieved should count in reality, however, there is a different situation at many companies. Regular reports can keep managers up to date and doubts can be proven wrong.
The previous investment in digitization is now paying off for companies. If documents and relevant information are available electronically and processes have been adequately, digitized, permanent work at home office is possible. The current crisis is driving the digitization of working life and integrating the internet into everyday work. If the home office is approached correctly, it can be more productive even for teams than in the office. However, the right hardware and software, a suitable workspace and way of working are essential. Challenges remain, but maybe this is the chance to try out home office with the entire team. In general, we all have to slow down the spread of the corona virus as much as possible and protect the weakest in society. Let us keep the Covid 19 disease rate as low as possible!
If you have any further questions, aixzellent team is available at any time by phone and email.
EuroStack: A secure and open path for Europe's digital future
EuroStack is a European industrial policy initiative that brings together technology, governance and funding for European-focused investments to build and adopt digital infrastructures. We support this and see important points here for future IT solutions.
In today's digital landscape, it is crucial for small and medium-sized enterprises (SMEs) to rely on secure and open IT solutions. The EuroStack initiative provides an excellent platform for this by bringing together European cloud services, open source technologies and interoperable tools that focus on transparency, data protection and sustainability.
As a German SME specialising in sustainable and customised IT solutions, we share EuroStack's vision. Our products and services are based on open source, are private and secure - perfectly tailored to the needs of our customers.
The critical developments in the US, especially with regard to data protection and digital sovereignty, emphasise the need to promote and use European alternatives. EuroStack enables companies to build their digital infrastructure on solutions that are in line with European values and thus strengthen our autonomy and competitiveness.
We support EuroStack and encourage other companies to join this initiative. By working together, we can create a strong, independent digital ecosystem in Europe that fosters innovation and protects our shared values.
We are available as a partner for companies looking for secure, open and customised IT solutions. Our expertise in areas such as groupware and cloud services enables us to develop customised solutions that are precisely tailored to your needs.
Let's shape Europe's digital future together - secure, open and sovereign.

Our proposal regarding the DSGVO: Data minimisation comes first!
Since protecting your data is our top priority and on the occasion of the entry into force of the new EU Data Protection Regulation (GDPR) on 25 May 2018, we would like to introduce our proposal for a privacy policy which emphasises the principle of data minimisation (Article 25) to you. To minimise the extent to which personal data are collected and processed, aixzellent completely renounces the use of external analytics tools such as Google Analytics.
Instead, the behaviour of users visiting our website is analysed completely anonymised and exclusively internally by ourselves with the open source web tracking tool Piwik. This means, in contrast to the use of Google Analytics, that collected data is never transferred to and/or used by any third party. In this way, we can also guarantee that all data is stored exclusively on servers in Germany and thus never transferred to any country with possibly questionable data protection regulations.
The full privacy policy for using our website can be found here. If you have any questions, please feel free to send us a message to sales@aixzellent.de!
Copyright reform – What you should know
 The Internet is no longer unknown territory. This basic consensus also prevailed in the European Parliament as it initiated the negotiations on a copyright reform. Now a decision has been made. On the final vote for the copyright reform 19 states voted in favor, six against and three abstained. As a conclusion the EU member states collectively approved the copyright reform.
The Internet is no longer unknown territory. This basic consensus also prevailed in the European Parliament as it initiated the negotiations on a copyright reform. Now a decision has been made. On the final vote for the copyright reform 19 states voted in favor, six against and three abstained. As a conclusion the EU member states collectively approved the copyright reform.
Why?
Through the reform authors of texts, pictures and videos should be better protected and fair payment should be ensured. The intention is to balance the claims of right-holders on one hand and users and online providers on the other hand.
How?
The package contains a total of 23 articles, two of those are highly controversial: Article 15 (formerly 11) and Article 17 (formerly 13):
- Article 11/15 – also known as ancillary copyright for publishers – is intended to establish a so-called ancillary copyright law which prohibits the use of protected works or parts of them without the consent of the authors. So all of those, who want to use the smallest excerpts of journalistic content on the web, need the publisher's license.
- Article 13/17 explicitly deals with user-generated content and thus with all websites where internet users can upload something. The article intends that these websites are forced to review any uploaded content for copyright infringement or to authorize them. In order to meet the simple abundance of content with software, it is feared that an upload filter must be introduced.
- Exceptions apply to platforms that are less than three years old or gain a maximum of 10 million € per year.
- In the protocol statement of the vote the Federal Government promises to interpret the definition of affected platforms in such way that Article 17 applies only to market-dominant platforms such as YouTube or Facebook.
It is still unclear how the requirements of copyright reform can be transposed into national law. It will take some time until the users will feel the change as the members of the EU have two years to implement them.
04/2020 Corona-Apps & Datenschutz? Machbar!
Corona-Datenschutz-Apps sollen die Verbreitung des Coronavirus‘ in Deutschland verlangsamen und wichtige Forschungsdaten erheben. Durch Rückschlüsse, wie sich das Virus ausbreitet, soll eine App entscheidend helfen. Vor allem das am 1. April 2020 vorgestellte “Pan-European Privacy-Preserving Proximity Tracing” (PEPP-PT) steht jedoch massiv in der Kritik von Datenschützer:innen. Die Bundesregierung hat sich nun offenbar für diese zentrale Lösung entschieden.
Folgende Apps sind in Deutschland bereits verfügbar bzw. noch in der Konzeption:
► Verfügbar: Datenspende-App des RKI
Eine Datenspende-App wird bereits vom Robert-Koch-Institut zum Download zur Verfügung gestellt. Mithilfe einer Smartwatch oder eines Fitnesstrackers werden Vitaldaten gesammelt und in anonymisierter Form dem RKI zur Verfügung gestellt. Auch diese App steht bereits massiv unter Kritik.
► Verfügbar: CoroNotes-App des Max-Plank-Instituts
Durch diese App wollen Forscher:innen vor allem den Krankheitsverlauf der Erkrankung besser nachvollziehen. In der Smartphone-Anwendung des Max-Plank-Instituts werden Fragen zu aktuellem Gesundheitszustand, Symptomen und Vorerkrankungen beantwortet.
► Verfügbar: Crowdless-App der ESA
Die europäische Weltraumorganisation ESA ist ebenfalls an einer Corona-App beteiligt, indem es das britische Start-Up Lanterne unterstützt. Dieses hat die Vermeidung von Menschenansammlungen zum Ziel. In der App des Unternehmens sollen über anonymisierte Daten von Google Maps und Google Places die Besuchszahlen der umliegenden Geschäfte ermittelt werden, um ein Ausweichen auf weniger gut besuchte Einkaufsmöglichkeiten zu ermöglichen.
► Noch in Arbeit: Corona-Warn-App der Bundesregierung
→ Geplanter Start: Ende Mai
Die Bundesregierung hatte für die geplante App drei unterschiedliche technische Konzepte in der näheren Auswahl. Mithilfe der sogenannten PEPP-PT-Technologie sollen per Bluetooth Infektionsketten schnell erkannt und Kontaktpersonen nachverfolgt werden. Auch der rivalisierende Ansatz D3PT (Decentralized Privacy Preserving Proximity Tracing) sowie die in Österreich eingesetzte Technik der Accenture GmbH wurden durch die Bundesregierung betrachtet und bewertet. Nun hat sich die Bundesregierung offenbar für die zentrale Lösung der PEPP-PT-Technologie entschieden und verspricht sich davon vor allem mehr epidemiologische Erkenntnisse.
► Noch in Arbeit: Apple & Google arbeiten an einer Corona-Warn-App
→ Geplanter Start: Mitte Mai
Ähnlich wie die PEPP-PT-Lösung soll auch die App dieser beiden großen Hersteller funktionieren. Eine entsprechende Bluetooth-Technologie soll zunächst als Grundlage für nationale Corona-Apps dienen und in einem zweiten Schritt direkt per Software-Update in die Betriebssysteme Android bzw. iOS integriert werden. Nutzer:innen sollen der Aktivierung dabei manuell zustimmen können. Ein Unterschied zum Ansatz der deutschen Bundesregierung ist die dezentrale Datenspeicherung, die angesichts der beiden Unternehmenshistorien für Verblüffung sorgt.
![]() Und der Datenschutz?
Und der Datenschutz?
Mehr als 300 Wissenschaftler:innen aus 26 Ländern warnen vor einer „beispiellosen Überwachung der Gesellschaft“ durch Corona-Apps, die keinen datenschutzkonformen Standards unterliegen.1 Dahinter steckt vor allem Kritik an dem Projekt PEPP-PT: Die Bluetooth-basierten Vorschläge könnten zum Teil eine Überwachung durch staatliche Akteure und private Unternehmen ermöglichen, die auf katastrophale Weise das Vertrauen in und die Akzeptanz für solche Anwendungen in der Gesellschaft beschädigten. Vorwürfe lauten unter anderem auch mangelnde Transparenz. So ist bspw. die Schweizer Firma AGT in das Projekt involviert, die vor einigen Jahren Massenüberwachungssysteme für arabische Staaten aufgebaut haben soll.2 Auch die zentrale Speicherung der Daten steht unter massiver Kritik. Dabei wird angenommen, dass es eine absolut ehrliche und zentrale Instanz gibt, die sich die gespeicherten Daten niemals anschaut oder weiterverwendet. Diese zentrale Instanz soll in Deutschland das RKI stellen, das jedoch bis heute keine Auskunft über zentrale datenschutzrelevante Problemstellungen geliefert hat.
Doch kann eine App ihren Zweck erfüllen und gleichzeitig Datenschutz gewährleisten? Ja, dezentral! Heutzutage können Netzwerke so aufgebaut werden, dass Daten nicht zentral gesammelt werden müssen. Durch die Art der Programmierung wird verhindert, dass Daten anfallen, die für eine Überwachungs-App missbraucht werden könnten. Man muss sich also nicht zwischen Hilfe zu Corona und Datenschutz entscheiden.
----------
1 Das gemeinsame Statement vom 20.04.2020 gibt es hier zum Nachlesen: https://drive.google.com/file/d/1OQg2dxPu-x-RZzETlpV3lFa259Nrpk1J/view
2 https://www.aargauerzeitung.ch/schweiz/umstrittene-firma-aus-zuerich-ist-in-geplante-corona-app-involviert-datenschuetzer-melden-bedenken-an-137683803
Home office tools: Not everything that glitters is gold...
(Open source) alternatives to commercial messaging and video conferencing tools
The current life situation is limited due to Covid-19. But possibilities of communication in home office are unlimited: Phones, private landline phones, chat programs, email, video conferencing and much more. The increase in home office jobs is pushing the use of collaboration solutions and video conferencing tools and giving them a boom that has never been experienced before. The increasing popularity is now fatal for many providers.
A look at well-known providers underlines the rush for messenger and video conference tools: Slack reports an increase in connected users from 10.5 to 12.5 million within a few days. Microsoft Teams has now passed the 44 million daily user mark. Google is also benefiting from the boom in virtual meetings: The use of Google's "Google Hangouts Meet" solution is 25 times higher than in January. Zoom was also able to benefit from the current situation. The video conference tool is most notably valued for its user-friendliness, its price structure and its simple deployment. But Zoom has now attracted a lot of criticism, especially when it comes to security: insufficient encryption of calls, security gaps, data exchange with Facebook or leaked emails and photos of users.
Fortunately, there are many exciting alternatives that are also available as an open source solution. We have selected three safe and user-friendly messenger and video conference tools for you:
 Mattermost, riot and Zulip
Mattermost, riot and Zulip
The web-based messaging solutions Mattermost, Riot and Zulip score with cross-platform availability. You have your own desktop clients as well as clients for mobile operating systems. Direct messages, group messages, archives and data transmission are available in all three applications. Riot also offers video and internet calls. These functions have so far only been available to a limited extent with Mattermost and Zulip. Riot can also score with end-to-end encryption; the other two services have transport encryption.
 Jitsi Meet, Kopano Video Meetings and Mikogo
Jitsi Meet, Kopano Video Meetings and Mikogo
Jitsi includes several open source projects that make it easy to conduct secure video conferencing. It was acquired by 8x8. The open-source software Jitsi Meet enables video conferences with one or more participants. In addition to video or audio chat, Jitsi Meet also offers the functions of desktop sharing and screen sharing of certain windows to present content. In addition, an integrated chat function is available to share text-based content with other participants. In addition to the web interface, Jitsi Meet is also available as an app on Android and iOS.
The device-independent software Kopano Video Meetings was developed for use in companies and allows "peer to peer" encrypted communication. It can be rolled out within a private cloud. Features include video and audio calls, one-to-one calls, and group calls.
You can display your own selected screen content via Mikogo and thus make it accessible to other authenticated users. Remote control of the screen is a big plus for this provider. After the necessary rights have been assigned, the presenter can take control of another computer and vice versa. With the integrated whiteboard function the presenter can also mark out screen contents or add comments. Locking and unlocking participants, recording sessions, and a session planner are also useful features.
----------
One last thing:
If you want full data sovereignty, you should set up your own server. If you lack the know-how or the time required to do this, many providers can host their own servers. We also take care of the setup, the individual configuration, the ongoing operation and the required power. We are always available for questions!
Challenges with mobility data
Digitization has long since made its way into the mobility sector and is placing increasing demands on the security of processes and systems. The early inclusion of suitable protective measures is mandatory for many institutions. Norms and standards describe general as well as specific requirements that are placed on an information security management system (ISMS). But collecting and merging mobility data is also a challenge.
As a division of Theis Consult GmbH, which operates as an engineering firm in the mobility sector, we deal with the relevance of data in the mobility sector on a daily basis. Data are a key to success for the mobility of the future. They can make mobility safer, cleaner and multimodal. While public transportation services in rural areas are often still inadequate, services in cities are not yet interconnected or are inadequately interconnected. Digital solutions are available for both challenges. But collecting and merging mobility data is proving to be a challenge. Simply expanding the infrastructure will not achieve the desired results. Instead, solutions are needed that keep an eye on the entire mobility situation at the local, regional and supraregional levels and thus make it possible to plan and manage. This can only be achieved if mobility flows are recorded universally. In theory, these can be best mapped using digital data. Up-to-date and reliable mobility information in real time enables mobility participants to plan their journeys optimally.
The demand for confidentiality of data and telecommunications is high, both from the business community and from consumers. Reliability, security and high availability are also the most important quality characteristics. This is one of the reasons why the transport and traffic sector is classified as a critical infrastructure (CRITIS), for which special protective measures must be taken. For this purpose, the BSI began 25 years ago to develop the IT-basic protection standards, according to which specifications for practice have been created at European and national level. Norms and standards describe general as well as specific requirements that are placed on a management system for information security. Local authorities, the administrations of the German Bundestag and the state parliaments, the audit offices of the federal and state governments, and the federal and state data protection officers are recommended to apply the guideline for information security.
 Currently, sensors on or near a road count the number of passing vehicles, among other things. It is also possible to record the volume of traffic, e.g., by determining the location of digital speedometers, which are already mandatory for newly registered trucks. In the future, more data will be added by cooperative, connected, and automated vehicles. As a national access point for mobility data, Germany already has the so-called mobility data marketplace, which will be transferred to the mobility data platform in the coming months together with the mCloud. Municipalities, cities and states also already collect (local) data. However, due to hierarchically structured responsibilities, each mainly takes care of its own areas, and there is a lack of capacity and know-how. In addition, long latency times cause difficulties or the data are not accurate enough. Reliable and comprehensive collection of mobility data is not possible and exchange between telematics systems is costly. The requirements and tasks that have arisen in the context of the CRITIS sectors also entail a not inconsiderable amount of work. They have an impact on all the planning steps of an infrastructure technology project, the roles of the players and the planning and implementation within them. The totality of infrastructural, organizational, personnel and technical components require, among other things, data protection concepts, the creation of general and specific guidelines and directives as well as one or more security concepts, risk analyses, emergency management, training, sensitization and much more. Every organizational level has to face responsibilities in the area of information security. Outsourcing the corresponding services is therefore an attractive time- and cost-saving option for many companies.
Currently, sensors on or near a road count the number of passing vehicles, among other things. It is also possible to record the volume of traffic, e.g., by determining the location of digital speedometers, which are already mandatory for newly registered trucks. In the future, more data will be added by cooperative, connected, and automated vehicles. As a national access point for mobility data, Germany already has the so-called mobility data marketplace, which will be transferred to the mobility data platform in the coming months together with the mCloud. Municipalities, cities and states also already collect (local) data. However, due to hierarchically structured responsibilities, each mainly takes care of its own areas, and there is a lack of capacity and know-how. In addition, long latency times cause difficulties or the data are not accurate enough. Reliable and comprehensive collection of mobility data is not possible and exchange between telematics systems is costly. The requirements and tasks that have arisen in the context of the CRITIS sectors also entail a not inconsiderable amount of work. They have an impact on all the planning steps of an infrastructure technology project, the roles of the players and the planning and implementation within them. The totality of infrastructural, organizational, personnel and technical components require, among other things, data protection concepts, the creation of general and specific guidelines and directives as well as one or more security concepts, risk analyses, emergency management, training, sensitization and much more. Every organizational level has to face responsibilities in the area of information security. Outsourcing the corresponding services is therefore an attractive time- and cost-saving option for many companies.
Statement: Why you cannot find us on facebook
Although facebook is the largest social network in the world, we have as a company decided not to have a profile on the platform due to various reasons. First of all, the privacy policy and the general terms and conditions (GTC) you have to agree to are extremely vague and user-unfriendly. Most notably, for any kind of service facebook offers you have to grant a permit to the corporation for a worldwide licence allowing it to collect and use all your contents (texts, picture, videos, messages, etc.), both provided by yourself but also by others. Consequently, the contents still belong to you but you have to transfer the control completely to the social network. Above that, facebook cooperates with third firms and shares the collected data with them, thereby also transferring them to the
Tracking Cookies - Currently still illegal!
Cookie Banner:
• The banners show an overview of all processing operations requiring consent, which can be explained and activated in function.
• Access to privacy and imprint may not be prevented by cookie banners.
• Before and while the banner is being displayed all further scripts from a website or web app are blocked if they can potentially capture user data. Only after approval, the data processing may actually take place.
• Without the option to refuse cookies it lacks the required voluntariness.
• A consent must be revocable as simple as possible.
As of late Cookie banners have been appearing almost everywhere. For most of the time they cover the content when visiting a website and require an "accept" or "ok". This could be seen as a direct implication of the General Data Protection Regulation which was released at the end of May 2018. Accordingly, this task should first have been taken over by the European E-Privacy Regulation, which still does not exist. Thus, shortly before the entry into force of the GDPR, a position paper was published which required explicit consent of users regarding site tracking mechanisms. Through creating a user profile these mechanisms are able to track the behavior of people on the internet. According to the position paper the informed consent must "be obtained in the form of a statement or other clearly confirming act before the data processing"1. From the beginning this special route of consent solution was very controversial.
 By examining 40 websites of larger providers in early 2019, the Bavarian data protection authority found out that not one provider meets all the strict requirements. Many of the currently displayed banners are clearly unlawful. Especially the missing option of rejecting cookie usage is a common problem. In addition, operators must present the processing of data to users in a transparent and comprehensible manner. In addition to a listing of the individual forms of processing, the function of a specific consent to individual forms of data processing is often absent. Only then will it be possible for users to make decisions with the complete knowledge of the specific situation and to understand the scope of the consent. It has to be acknowledged that in specific cases, the interest of the website provider has to be weighted with the interest and the fundamental rights and freedoms of the individual user. Even after a year, there is still much legal uncertainty in this area.
By examining 40 websites of larger providers in early 2019, the Bavarian data protection authority found out that not one provider meets all the strict requirements. Many of the currently displayed banners are clearly unlawful. Especially the missing option of rejecting cookie usage is a common problem. In addition, operators must present the processing of data to users in a transparent and comprehensible manner. In addition to a listing of the individual forms of processing, the function of a specific consent to individual forms of data processing is often absent. Only then will it be possible for users to make decisions with the complete knowledge of the specific situation and to understand the scope of the consent. It has to be acknowledged that in specific cases, the interest of the website provider has to be weighted with the interest and the fundamental rights and freedoms of the individual user. Even after a year, there is still much legal uncertainty in this area.
GDPR-compliant e-learning with BigBlueButton, Moodle and Nextcloud - data protection begins with the little ones
 In the academic corona crisis, teaching has suddenly shifted from school to digital space. The domestic classroom poses new challenges for everyone involved. We think: Schools have to rely significantly more on data protection-compliant, decentralized and open-source solutions in homeschooling! Because, while restaurants and cafés are opening again in Germany, school operations remain anything but normal. The use of digital open source solutions is required here. We introduce BigBlueButton and our favorite combination.
In the academic corona crisis, teaching has suddenly shifted from school to digital space. The domestic classroom poses new challenges for everyone involved. We think: Schools have to rely significantly more on data protection-compliant, decentralized and open-source solutions in homeschooling! Because, while restaurants and cafés are opening again in Germany, school operations remain anything but normal. The use of digital open source solutions is required here. We introduce BigBlueButton and our favorite combination.
BigBlueButton (BBB for short) is a web conferencing system for e-learning.
The platform enables the common use of multiple video and audio formats, a whiteboard, a chat, jointly editable notes and a screen sharing function in real time. Additionally, lessons and lectures can be recorded.
Tools tailor-made for teachers
Teachers can share their audio data, slides, chats, videos and desktops with the students. Integrated surveys also make it easy to involve students in the classroom. When using the whiteboard tool, the information entered is made available to the students in real time. Teachers have the option to zoom into presentation slides, to highlight them and to draw and write in them. This results in a visual improvement in the classroom.
BBB for group work
The fact that a BBB activity can be opened for a work group also enables group work without moderation. The room initiator can give all participants moderation rights so that they can use all functions in BBB. Every participant in an online group work is free to use their own webcam. This makes it possible, for example, that requests to speak can be signaled using hand signals. Furthermore, participants can chat with each other and exchange information.
The simple API makes it easier to integrate your own products and scores with a long list of available integration options with third-party applications such as Canvas, Drupal, RedMine, Wordpress and much more. BBB can be integrated into Moodle LMS, so that participants who did not take part in a live session can view it later.
It also enables students to access materials for the webinar and other activities such as submissions of tasks, discussions in forums, creation of a joint results protocol in wikis etc.
Data protection
The video and web conference system is encrypted with SSL due to strict data protection regulations. The server location is in Germany, however BigBlueButton can also be operated on its own servers. The data transmission is additionally secured by SRTP, which is suitable for the encrypted transmission of communication over the Internet. Another positive feature: The recording of the lessons requires the data protection consent of all those involved before the recording begins.
More information about BigBlueButton is also available at https://www.aixzellent.com/en/premium_e-learning
![]() Our favorite combination: BBB, Moodle & Nextcloud
Our favorite combination: BBB, Moodle & Nextcloud
BBB and Moodle can be integrated in Nextcloud, so that the functions can be used, which are suitable for schools and teamwork. A secure data exchange, a course management system, simple operation and the use of the other collaboration tools in Nextcloud such as OnlyOffice, Chat, a calendar etc. make this combination particularly attractive. In addition, BBB and Moodle can only be hosted in Germany through the integration in Nextcloud, so that a GDPR-compliant operation is possible.
More Information about the Nextcloud is also available at https://www.aixzellent.com/en/premium_privateclouds
The (partial) closure of schools and other educational institutions leads to great uncertainty. It is clear that with the right e-learning tools, protect not only the smallest of our society, but teachers and students can be relieved and lessons at home can be made as attractive as possible. If schools and other educational institutions are now not ready to choose secure solutions in favor of data protection, in the long term, this will be at the expense of privacy and data protection.
Data protection-compliant work from home: decentralized and open source
Corona has shown: Working from home is possible in many companies. Some studies showed that more than half of the germans wished to flexibly work from home even after the current pandemic. The german Federal Minister of Labor, Hubertus Heil, even asks for a right to work from home office. It’s now in the hands of the companies to provide data protection-compilation, decentralized and open source solutions for their employees.
We advise against the usage of applications with centralized data storage, as the integrity of your data is not fully under your control. For months Zoom is making news with security issues, like only providing E2E-Encryption for text messages, but not for audio and video streams. Instead Zoom uses TLS, the transport layer security. As a result Zoom still has full access to transferred data, like video and audio data, after a conference ended. Microsoft (Teams) also got negative press about security and data protection-compliant practices. Extending to that Microsoft also collects a lot of data over standard applications without informing their users. Another problem is related to the ‚CLOUD Act’, which rules US companies to share their data to government agencies in case of investigations. Even if the location of the data storage is not in the USA itself and even if the local jurisdiction forbids the sharing of this data.
 We advise against the usage of applications with centralized data storage, as the integrity of your data is not fully under your control. For months Zoom is making news with security issues, like only providing E2E-Encryption for text messages, but not for audio and video streams. Instead Zoom uses TLS, the transport layer security. As a result Zoom still has full access to transferred data, like video and audio data, after a conference ended. Microsoft (Teams) also got negative press about security and data protection-compliant practices. Extending to that Microsoft also collects a lot of data over standard applications without informing their users. Another problem is related to the ‚CLOUD Act’, which rules US companies to share their data to government agencies in case of investigations. Even if the location of the data storage is not in the USA itself and even if the local jurisdiction forbids the sharing of this data.
We advise against the usage of applications with centralized data storage, as the integrity of your data is not fully under your control. For months Zoom is making news with security issues, like only providing E2E-Encryption for text messages, but not for audio and video streams. Instead Zoom uses TLS, the transport layer security. As a result Zoom still has full access to transferred data, like video and audio data, after a conference ended. Microsoft (Teams) also got negative press about security and data protection-compliant practices. Extending to that Microsoft also collects a lot of data over standard applications without informing their users. Another problem is related to the ‚CLOUD Act’, which rules US companies to share their data to government agencies in case of investigations. Even if the location of the data storage is not in the USA itself and even if the local jurisdiction forbids the sharing of this data.
We introduce ideal and data proctection-compliant tools for home office, which already proved themselves worthy.
Team chat tools
- Mattermost is a fulll open-source alternative to Slack. It provides the same features like Slack: public and private chat rooms, person-to-person chat, data sharing, customizable emojis, web hooks, slash-commands and multi language support.
- Riot is a multi platform open source software for chat, IP/video calls over the matrix protocol stack, which already hosts existing communication mehtods like IRC, Slack, Twitter, Telegram and Apple iMessage.
- The group chat application Zulip is easily integrated with popular software development tools, like GitHub and Jenkins. Private and topic-based group chats, data storage of all data in a stream, private chats, status flags, data uploads, emojis and e-mail or desktop notifications are a few features of Zulip.
Your can find more information at our team chats.
Web meetings
- The open source software Jitsi can host video conferences with one or multiple participants. Beside video and audio chats Jitsi Meet also provides desktop sharing and screen sharing of specific windows to present your content to others.
- Kopano Meet is a video conference tool, which works independent from the Kopano apps. The installation doesn’t require the usage of other apps.
You can find more informations here.
Our recommendation for conferences:
BigBlueButton s a online conference system, which also suits for e-learning. The platform provides the shared use of multiple video and audio formats, a whiteboard, chat, shared notes and real-time screen sharing. Additionally lessons, lectures, seminars or presentations can be recorded.
Ask us about a selection of a suitable tool for your company or private use case - we are happy to advise you in a not binding exchange.
Is there no alternative to the use of the most popular social media & messenger services? Not at all!
Almost everyone uses social media and messenger services every day... But why is this almost exclusively limited to Twitter, Facebook, WhatsApp and Co.? The most obvious answer seems to be: Because most people are active in these networks which allows a particularly broad range – both to reach others as well as to be heard by others. If everyone persists on this viewpoint, unfortunately, nothing will ever change – although there are much more good reasons to use alternatives than to stick to the most widely used networks, thereby supporting their monopoly.
If you want to make use of services like Facebook, Twitter, WhatsApp and Co., it is unavoidable to agree to the general terms and conditions as well as to the data protection guidelines. But honestly, who reads all this every time? This is even though everyone should always have read everything in the small print to give consent consciously. In the currently valid terms and conditions of Facebook (as of January 30, 2015), for example, users explicitly must give their permission to a worldwide license which allows the platform to use all published contents (texts, photos and videos) which are actually protected by the right of intellectual property.
This means that ownership and control over all published content must be handed over to third parties forever and irrevocably, while allowing Facebook additionally to collect and use this information for its own purposes. If you do not want this, you de facto cannot use the network anymore. This should be clear to everyone. With Twitter, it does not look much better. Regardless of the country from which you provide your data, you must authorise the company to reuse all information in the US and in any other country in which it is active. Consequently, it remains perfectly unclear where personal data are spread and used.
The updated terms and conditions of WhatsApp published last year make the use of the service almost impossible, too, since you must confirm that you are authorised to transfer the contact data saved in your address book to the company. Not a single user of the messenger has probably obtained such permission from each individual contact. Consequently, the use of such services does not only lead to a negligent handling of one’s own data, but also of those of completely uninvolved third parties. Even worse – this does of course also affect those who have deliberately decided to use alternatives to protect themselves against this madness. Therefore, it should be clear to everyone that everybody does not only bear responsibility for his own data, but also for those of others.
This should rouse even those with a “I do not care attitude” at the very latest and motivate to use services such as Diaspora, Mastodon, Signal and Co. Instead of storing data on huge central servers belonging to large organisations located in regions with questionable privacy guidelines, local servers (pods) can be set up anywhere in the world for the free use of the social network Diaspora. Therefore, you do not only decide with which pod you want to register, but you will also always preserve the rights over your data. Another decentralised free alternative on open-source basis is the 2016 in Germany developed microblogging service Mastodon.
Here, so called toots are posted instead of tweets. In addition to the self-determination how the content of these toots will be used, they allow the utilisation of up to 500 characters. Moreover, there is a particularly recommendable alternative to the messenger service WhatsApp taken over by Facebook in 2014 which treats data security as top priority. If Open Whisper Systems was forced to release data from Signal users and their communication, the company would only be able to provide their registration date and the time of the last login. Everything else is neither visible nor saved, but is encrypted just as any content.
The bottom line is that Diaspora, Mastodon, Signal and Co. are clearly more transparent and user-friendly platforms than Facebook, Twitter, WhatsApp and Co., on which the user, his interests and, above all, data security are clearly in the focus. All laws for the protection of personal data will be ineffective and useless if providers constantly disregard them, while users support this behaviour by using such services. Therefore, anybody should constantly ask him-/herself whether he/she is aware of and constantly giving sufficient consideration to this responsibility. If this question cannot be answered with a clear “yes” in any case, it will be high time to build up a second mainstay, as well as to convince family and friends to also use it exclusively in the long term.
Further services, information and comparisons are available via http://alternativeto.net abrufbar.
[Sources: https://de-de.facebook.com/legal/terms, https://twitter.com/de/tos, https://www.whatsapp.com/legal/?l=de, https://diasporafoundation.org/, https://mastodon.social/terms, https://whispersystems.org/, https://www.aixzellent.com/de/facebook]
Ready for the GDPR from the perspective of website operators
With the entry into force of the European Data Protection Regulation (EU-GDPR) on 25 May 2018, the fear of warnings and fines has increased significantly, especially for small and medium-sized enterprises (SMEs). However, only time will show the actual impact on website operators and SMEs. Risks can be minimised though if one knows the new legal basis and is able to react to it at short notice if necessary.
The most important thing to know is that the GDPR affects everyone, including you! Whether privately or professionally, everyone has to do in some way with personal data and should therefore familiar with the Europe-wide almost uniform data protection rules, at least in broad terms. The good news is: Since large parts of the GDPR are based on the strict German data protection law, you will probably already know some regulations.
Our recommendation to website operators is to pay particular attention to the principle of data minimisation. In this context, we have reduced the scope of collecting and processing personal data to an absolute minimum as well. Moreover, we completely disclaim the use of external analytical tools. However, if you cannot refrain from gathering certain data and integrating external services, you should bear the following in mind:
Data minimisation: Only personal data may be collected which are absolutely necessary for the purpose. For instance, to register for a newsletter, only a valid email address is absolutely necessary, that means neither name nor date of birth or the like are required.
Purpose limitation: The purpose for the collection, storage and processing of personal data must have been previously clearly defined and may not be changed or extended without separate consent.
Prohibition with permission: Personal data may not be collected, stored and processed unless there is a clear legal basis or consent of the person concerned.
Data transfer: Personal data may never be shared with third persons or passed on to third parties without explicit permission. A particular challenge for website operators is the integration of non-European services such as Google Analytics.
Order processing: You should conclude an "order data processing contract" with any external service provider who comes into contact with the personal data you have collected from your customers with obliges each external provider to treat these data in accordance with DSGVO as well.
Tracking: You must inform the visitors of your website about any kind of user tracking. For instance, this includes already the anonymised storage of IP addresses. Likewise, the first time a visitor enters a website, its operator must indicate the use of cookies and implement an opt-out option that can be used to decline the use of cookies.
Encryption: In the case of web forms, logins, contact forms or shop orders, personal data must be transmitted with SSL encryption (https: //).
Clarity and transparency: You must provide a clear privacy policy directly on the home page of your website which informs your visitors about how their data are handled. Moreover, it must be clearly formulated and understandable to anyone. In addition, you must create consent texts for the collection of data and make clear that the agreement may be revoked at any time.
Documentation and accountability: As a website operator, you are obliged to record processes which are connected to personal data in directories and to provide them on request to regulatory agencies.
Obligation to inform and report: As a website operator, you are generally obliged to provide free information about stored personal data. In addition, you must report the loss of personal information to supervisory bodies immediately in order to minimise or avoid fines. Non-compliance with the new data protection rules will also be fined.
Data Protection Officer: If your company has at least ten employees who are permanently involved in the processing of personal data, you must appoint a data protection officer who oversees all operations and acts as connector between operator and supervisory authority.
With these briefly summarised key regulations, we would like to support you in their implementation and hope that we could give you a good introduction and overview. For questions and suggestions, we are always happy to help and wish you all the best and success for your website! [Source: Kompac't 1/2018].
Privacy Shield Judgement - Privacy vs mass surveillance
This month the austrian lawyer Max Schrems was successful in front of court: The european court ruled the Privacy Shield invalid. Reason: Our european data protection laws can’t be followed in the USA. The US regards their national safety over that of private personal data and the right for effective judicial legal protection. Laws like the Foreign Intelligence Surveillance Act (FISA) resulted in mass surveillance without a legal reason, which is not combinable with european law.
 Privacy Shield: Legal framework for transatlantic data traffic, which rules that the US data privacy laws are sufficient for the data traffic of personal data by companies like Facebook and Google. In return the USA gave limited guaranties for restricting their mass surveillance of european users.
Privacy Shield: Legal framework for transatlantic data traffic, which rules that the US data privacy laws are sufficient for the data traffic of personal data by companies like Facebook and Google. In return the USA gave limited guaranties for restricting their mass surveillance of european users.
Until now, European data on American servers was exposed to surveillance by US authorities without protection. US companies such as Facebook or Google, which have little interest in strong data protection, also bear joint responsibility - after all, this stands in the way of business models with personalized advertising. At the latest after the revelations of the whistleblower Edward Snowden it is also clear: The NSA is sucking in data from Apple, Facebook, Google and Co. on a large scale and also making them available to other US authorities. Since there is no way to find out if you are being monitored, people also have no way to go to court. In this context, the ECJ even spoke of a violation of the “essence” of EU fundamental rights.
 What now follows the judgment is a massive legal uncertainty: Although international data traffic is still possible, the fundamental rights of EU citizens must be observed - a complex task. Data protection officers in Germany and Europe must quickly come to an agreement on how to deal with institutions that continue to rely on the Privacy Shield in an impermissible manner. The often used standard contractual clauses (SVK) can still be concluded in principle, however, before the first data transmission, it must now be checked whether there are state access options to the data abroad.
What now follows the judgment is a massive legal uncertainty: Although international data traffic is still possible, the fundamental rights of EU citizens must be observed - a complex task. Data protection officers in Germany and Europe must quickly come to an agreement on how to deal with institutions that continue to rely on the Privacy Shield in an impermissible manner. The often used standard contractual clauses (SVK) can still be concluded in principle, however, before the first data transmission, it must now be checked whether there are state access options to the data abroad.
Schrems said:
„The Court of Justice has now made it clear for the second time that there is a conflict between EU data protection law and US surveillance law. Since the EU will not change its fundamental rights to satisfy the NSA, the only way to overcome this conflict is for the US to introduce solid data protection rights for all people, including foreigners. Surveillance reform will be critical to Silicon Valley's business interests.“
One thing is certain: until the legal situation changes, according to the judgment, personal data should no longer be transmitted to the USA as before. Only when the NSA and other (American) secret services are put a stop, we can speak of a similar level of data protection between the EU and the USA. Until then, companies, public administration and European supervisory authorities have the task of applying the ruling. Despite the declarations of invalidity in the judgment, absolutely "necessary" data transfers can still take place in accordance with Article 49 GDPR. If users want their data to flow legally abroad, there are still options. The data transfer can be based on the informed consent of the user, which can be revoked at any time. The GDPR also allows data transfers that are "necessary" to fulfill a contract. We therefore continue to advise against using centralized american service providers such as Facebook. We published a statement on Facebooka few years ago.
----------------------------------------
1 https://netzpolitik.org/2020/eugh-zum-privacy-shield-schuld-ist-das-system-der-massenueberwachung/
IT security with aixzellent
As awareness of secure IT continues to grow, we are also receiving more and more inquiries regarding the security of our systems. We have now summarized the most important information.

Your servers
Servers that we set up on behalf of our customers are hosted exclusively in Germany in compliance with the EU-GDPR, unless the customer requests otherwise. Hetzner has long been the data center we trust and it is certified according to DIN ISO/IEC 27001. The certificate proves adequate security management, data security, confidentiality of information and availability of IT systems. It also confirms that security standards are continuously improved and monitored on a sustained basis.
Physically, Hetzner's data center parks are broadly protected. The security systems include a high-security fence, video surveillance, visitor badges, access authorizations, transponder chips and an early fire detection system.
The networks, systems and data are also broadly secured on the part of Hetzner. DDOS protection, firewalls, security updates and backup servers make this possible. More information about security at Hetzner is available [here].
Your systems
Setup
Our systems are all configured and operated with special attention to information security (CIA: Confidentiality, Integrity, Availability). We make sure that only really necessary accesses are directly accessible from the Internet. Everything else is only accessible from our management network to minimize attack surfaces from outside. Automatic provisioning and 2-factor authentication are also standard for the management services set up.
24/7 monitoring
The security of your data and communications is our top priority. Your systems are therefore monitored on an ongoing basis. For their part, the systems and procedures used are subject to constant maintenance and updating, so that your systems and data are also protected against the latest methods of attack. In addition to the "classic" passive security measures, we also rely on procedures such as "Active Defense".
Communication always encrypted
In addition, we support the highest possible security standards and always transmit data exclusively via an encrypted SSL/TLS connection. We generally use validated certificates for this, which are set up on your systems. This ensures the highest standards. We usually only allow exceptions to encrypted communication for your websites and as a fallback solution, e.g. for the mail server (server-to-server communication), as unfortunately there are still mail servers on the Internet that cannot handle secure encryption.
Regular backups
Regular backups, which are also stored encrypted on separate hard disk storage (RAID5), form the basis for your long-term data security.
Our employees
The employees responsible for setting up and managing your servers are certified as BS basic protection practitioners.
More security (e.g. through HA, VPN, additional encryption etc.) can of course always be added in individual cases!
Do you have further questions? Please feel free to contact us at any time!
Nextcloud: Additional possibilities for data management with aixzellent
Nextcloud is a new, free cloud server software on the basis of the ownCloud version 9. Besides further available functions, there are above all specific business functions (Enterprise Support) which are all open source. Accordingly, the server platform is suitable both for private use as well as for companies to guarantee access to all data, to be able to synchronise and share them. In addition to that, great emphasis is placed on privacy and security. You decide what information you store in your cloud, where it is hosted and who can access it. Sharing REST API allows you to monitor and control which data you share using mobile apps or desktop clients. The WebRTC Conferencing and the support of Spreed.ME offer you the possibility to perform videoconferences securely and exchange short messages through a chat. Of course you can access your data, contacts, calendar, etc. from anywhere and easily add new functions to optimise the use of the external storage to suit your personal needs optimally. aixzellent hosts and maintains your cloud, which we can also set up on the basis of Nextcloud on request. Get in touch with us, we will be happy to advise you!
08/2017 – With aixzellent you will find the perfect fitting security solution for your SME!
More than 50 % of all German companies have been victims of digital economic espionage or data corruption in recent years. And yet, the estimated number of unreported cases is much higher. In addition, such attacks are no longer confined to large companies and corporations. Small and medium-sized enterprises (SMEs) have to deal intensively with the safeguarding of their data and company values since specifically here most of the necessary security measures, resources and know-how are lacking. For this reason, in particular SMEs need cost-effective and easy-to-operate security solutions which offer comprehensive and reliable protection with little effort.
Virus scanners and firewalls are usually existing but are often insufficient to protect SMEs reliably from data theft, abuse and cyberattacks since hackers know many other loopholes like for instance security gaps in the domain name system (DNS) to get into enterprise networks. The impact of such cyberattacks is as serious as versatile. Sensitive data is lost, company secrets are spied on and the reputation of a company is also at stake because both partners and customers alike rely on the security of their data. Once this confidence is shaken, it will be very difficult to restore it.
Moreover, SMEs are also increasingly faced with the challenge that more mobile employees are (partially) working from home or in the distribution of customers and partners. Also in these cases, the full security of all company data must also be fully ensured. The key to an optimised IT security success for SMEs is usually a combination of security solutions. For example, a cloud provides a comprehensive protection of the IT infrastructure with which stored data can be retrieved and used at any time. The administration of all contacts, appointments, calendars, etc. is made possible by a groupware solution while VPN allows secure access to company networks from anywhere.
These are just a few examples of many flexible, tailor-made managed hosting solutions that we design and implement specifically and individually for SMEs. The special thing is that your data are hosted exclusively on servers in Germany and are therefore not transmitted in countries with questionable to completely inadequate data protection laws. With the help of automated provisioning and monitoring systems, we also maintain and monitor your systems 24/7 securely, efficiently, cost-effectively and are at your disposal with advice, support and assistance at any time. Interested? Please do not hesitate to contact us for a free, personal consultation right away! [Source: https://www.security-insider.de/so-klappt-es-mit-der-it-sicherheit-im-mittelstand-a-630567/]
GDPR for Consumers: Power to the People
The GDPR can mean a lot of work for companies which have not yet dealt with the topic of data protection and might therefore be perceived as disadvantageous. However, this should not be the case because those working with personal data have a certain responsibility to protect them. Therefore, we advise website operators to be as economical as possible in collecting, storing and processing such data. Please see in this regard also the summary of key points for handling personal data (07/2018).
For consumers, the standardisation of European data protection directives is in any case a great benefit and success. One thing is of particular importance to this end: Customers must be informed in more detail how their personal data are used and they have the right to object to this use at any time. To provide a precise idea about which rights consumers will exactly have in the future and how they can benefit from the GDPR, the following summary provides an overview of the most important innovations and what they mean for you.
Scope: The GDPR applies to all EU citizens whose rights it strengthens. Companies are from now on obliged to provide information about which personal data they collect, process and store for what purposes and how long. This also applies to any company which is not based in the EU as soon as they direct offers to European consumers. Thus, it applies to major US companies such as Google, Facebook and Co. as well.
Privacy by default: Essentially, only those personal data should be collected and processed which are absolutely necessary! This means also that companies are required to take care of data protection-friendly default settings. For example, when placing an order via a web shop, the name and delivery address are indispensable. The phone number is for instance not necessary to process the order and should therefore not be mandatory. In addition, companies may of course offer their customers to subscribe to their newsletter by activating a corresponding op-in box. This box should, however, not be pre-activated. Also regarding apps, for example, the microphone or access to photos etc. may not be enabled automatically.
Duty of information/plaintext: Since the GDPR came into force, companies have to inform their customers in detail about the purpose, the processing and the duration of storage of their personal data. However, this must be easily understandable for anyone and limited to the necessary minimum. A clearly formulated privacy policy should be available directly on the homepage of each website. If any data is passed on to third parties, the consumer must be informed about who will get access to his/her personal data. In addition, he/she must explicitly agree to this data transfer. Should there be any incident regarding a customer’s personal data, companies are obliged to inform him/her about this without delay.
Answer/information obligation: Companies have to inform consumers on request about their rights. In addition, they must provide any information about what data they have currently stored, for which purpose, for how long, as well as if and to whom they will be given. Such requests must be processed free of charge within four weeks.
Data Degradation & Right to Forget: Consumers have the right to request the immediate and complete deletion of stored personal data at any time. This right excludes for instance billing information which must be stored under German law for 10 years. Likewise, companies are obliged to destroy personal data immediately after the expiry of such deadlines or if the purpose of the storage has ceased to exist.
Data Copy & Data Portability: Companies must provide their customers on request with an electronic copy of their personal data, for instance as PDF. Moreover, they should for example in the event of terminating a contract provide the consumer with his/her data in a common electronic format in order to facilitate his/her migration to another provider.
Supervisory authorities: Customers have principally the right to address the responsible supervisory authority for any data protection concerns or doubts.
Although some of the provisions and wording of the new EU data protection directives are not yet fully defined, the GDPR is overall a big step in the right direction, finally allowing consumers extensive rights which are fully justified. Please do not hesitate to contact us if you have any questions, we will be happy to help. [Source: Kompac't 1/2018]
Consent-free tracking with Matomo as an alternative to Google Analytics
With 80% market share, Google Analytics is the undisputed market leader among web analysis services. But it has its downsides: the data quality is in need of improvement, is commercial and, above all, legally not harmless. As an open source web analytics platform, Matomo, formerly Piwik, is a real alternative to Google Analytics and, with the right use, website operators can even dispense with the use of cookie banners.
One of Matomo's guiding principles is “respecting privacy” - even if this initially seems to contradict a web analytics platform that tracks user activities on websites. But Matomo can be configured in such a way that the strictest data protection guidelines are observed. This is made possible by expanded data protection functions: For example, the software has an opt-out mechanism with which users can deactivate web analysis tracking. It is also possible to anonymize IP addresses and implement other data anonymization techniques. Expiration dates for tracking cookies can also be set. Further information is also available at https://matomo.org
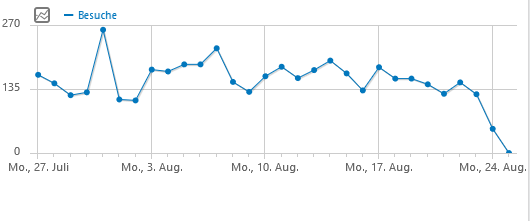 There are currently two Matomo tracking variants: JavaScript fingerprinting or server logfiles. Both variants have their advantages and disadvantages. Variant one is comparatively easy to set up and the recognition of returning visitors works much better. Advanced use cases (use of more precise metrics, recording of heat maps, form analyzes, etc.) and the recording of outgoing links are also possible with this variant. On the other hand, variant two scores with the fact that JavaScript does not have to be integrated into the context of the page. In addition, the log file also contains visitor information if advertising and tracking blockers are used, and spambots can be more easily identified and filtered. The technical functionality of both variants as well as the configuration of the log file analysis are described here well and in detail. A clear recommendation for variant two is also given here:
There are currently two Matomo tracking variants: JavaScript fingerprinting or server logfiles. Both variants have their advantages and disadvantages. Variant one is comparatively easy to set up and the recognition of returning visitors works much better. Advanced use cases (use of more precise metrics, recording of heat maps, form analyzes, etc.) and the recording of outgoing links are also possible with this variant. On the other hand, variant two scores with the fact that JavaScript does not have to be integrated into the context of the page. In addition, the log file also contains visitor information if advertising and tracking blockers are used, and spambots can be more easily identified and filtered. The technical functionality of both variants as well as the configuration of the log file analysis are described here well and in detail. A clear recommendation for variant two is also given here:
Against the background that the ECJ ruling of October 2019 can also be interpreted in such a way that the visitor has to give his consent to the tracking even with the variant with JavaScript fingerprinting (without cookies), the advantage here is clearly with the log file analysis.
In terms of functionality, Matomo clearly competes with Google Analytics. In contrast to this, it can also be used without the active consent of website visitors, provided that the log file analysis is used: Small to medium-sized websites in particular can benefit from Matomo, as they - with the correct structure of their website - can dispense with the use of cookie banners. Website operators can either host Matomo themselves or with a provider in the cloud. If Matomo is operated on its own servers, compliance with data protection can be verified, as the data collected is not automatically shared with a third party.
Private clouds in companies
Cloud computing is no longer a future trend, but rather a fundamental component of modern IT strategies. However, while public cloud offerings were long considered the ultimate solution, a shift in thinking is increasingly emerging: more and more companies are turning to private clouds to control costs, meet regulatory requirements, and better protect sensitive data. As an IT service provider focusing on customized infrastructure solutions, we at aixzellent see the private cloud not only as a secure alternative, but also as a strategic success factor for the digital future.
Private clouds are preferred by companies for a variety of reasons. These include cost, complexity, and compliance. Public clouds score points for elasticity and scalability—but with data-intensive and sensitive applications, the risk of unpredictable costs and lack of control is becoming increasingly apparent. Especially in the AI environment, where data locations and access rights are strictly regulated, the private cloud is becoming increasingly relevant.
Advantages of the private cloud for customers
- Cost control: Automated lifecycle management, memory tiering, and demand-optimized configurations enable sustainable reductions in licensing, storage, and operating costs
- Reduced complexity: Consistent tools and a virtualized platform across all IT silos enable faster DevOps processes and strengthen innovation
- Legal certainty and data protection: Companies retain full control over the location, access, and processing of data—essential in the context of GDPR, NIS2, and the EU AI Act
The success of the private cloud is not just a passing trend—it is a strategic transformation driven by cost pressures, complexity reduction, and regulatory requirements.
As an experienced IT company, we at aixzellent can help our customers navigate this change safely and efficiently—from consulting and technology to operations.

aixzellent als Marke eingetragen
Im Spätsommer 2012 wurde die Marke aixzellent erfolgreich in das deutsche Markenregister eingetragen. Sie wird seit dem für die erfolgreichen IT-Services der Theis Consult GmbH genutzt. Wir bündeln hier unsere Erfahrungen und unser Know-How in allen Fragen der IT-Beratung, -Konzeption und -Entwicklung für die öffentliche Verwaltung, KMU und Ingenieurbüros.
With aixzellent your data & systems are safe: Hetzner offers free DDOS-protection
The protection against DDOS (Distributed-Denial-of-Service) attacks is a service offered free of charge for all clients of the Bavarian hoster Hetzner and therefore also for our aixzellent customers whose data are hosted exclusively on German servers provided by our partner Hetzner. Making use of Juniper and Arbor hardware applications, websites, server, web applications and IT-infrastructures are protected against the risks and dangers deriving from DDOS-attacks. Your incoming traffic will be scanned with regard to known types of hazards which will then automatically be detected and filtered out. In order to provide an adequate response to DDOS-attacks, the systems are above that also able to distinguish between an UDP- and a SYN-packet flood. Since the DDOS-protection is always active automatically, there is neither the need to activate it, nor will it influence your traffic at all. Therefore, take the opportunity to protect your data and systems with aixzellent in the best possible way. In case you have questions or would like to take advantage of a personal consultation please to not hesitate to contact us right away. [Sources: Hetzner]
End-to-end encryption (I)
Increasing cooperations between IT companies and states – Is this the end of secure messaging in Germany?
Billions of data with a standard end-to-end encryption are sent and received daily. Meanwhile the surveillance interests of states and authorities are steadily increasing. For years opponents and proponents of encryption have been forming worldwide.
 Many states want to massively expand the hacking capacity of state authorities: Not only authoritarian regimes but more and more western democracies nowadays see encrypted communication as a major threat to public safety. They demand to weaken encryption of communication and the ability to use spyware on smartphones. The encryption keys are managed by large Internet corporations, which can also specify who can access the plain text secretly. Access to these cloud systems or hardware implants for preempted data traffic interception is becoming more and more a focus. The big Internet companies such as Facebook, Google or Amazon are now so powerful that states seek to cooperate with them and the interests of users are taken less care of. The opponents demand a strong and secure encryption which, however, at the same time cannot interfere with investigations. However, a concrete and feasible implementation of such a technical solution does not exist yet.1
Many states want to massively expand the hacking capacity of state authorities: Not only authoritarian regimes but more and more western democracies nowadays see encrypted communication as a major threat to public safety. They demand to weaken encryption of communication and the ability to use spyware on smartphones. The encryption keys are managed by large Internet corporations, which can also specify who can access the plain text secretly. Access to these cloud systems or hardware implants for preempted data traffic interception is becoming more and more a focus. The big Internet companies such as Facebook, Google or Amazon are now so powerful that states seek to cooperate with them and the interests of users are taken less care of. The opponents demand a strong and secure encryption which, however, at the same time cannot interfere with investigations. However, a concrete and feasible implementation of such a technical solution does not exist yet.1
Nevertheless, the pressure on suppliers is increasing and is currently very high, especially in the USA. Germany’s position is contradictory, but a turn away from a German cyber security policy seems more and more likely.
"This is demonstrated by the BKA law of June 2017, which legitimizes the use of surveillance Trojans on end devices such as smartphones, or the creation of the Central Information Security Authority (ZITiS), which is to develop the same surveillance solutions. While the encryption software remains technically untouched, the communication on the terminals should instead be read out before encryption by means of state monitoring software."2
In June of this year, according to plans of the Interior Ministry, encrypted messenger services should be forced to set up a listening interface.3 Thus, the operation of a secure messenger within Germany will no longer be possible.
----------
1 https://netzpolitik.org/2018/fbi-klagt-ueber-verschluesselte-handys-mal-wieder/
2 https://netzpolitik.org/2017/stiftung-wissenschaft-und-politik-warnt-vor-schwaechung-der-verschluesselung/
3 https://www.golem.de/news/crypto-wars-protest-gegen-entschluesselungszwang-bei-whatsapp-co-1906-141825.html
Industry 4.0 for SMEs – IT of the future with aixzellent
The increasing digitalisation and interconnection of the fourth industrial revolution changes the entire production chain while multiplying the worldwide data stock. In order to be able to properly evaluate and use these gigantic data sets one must not only understand but also know how to extract the really useful data from them. In addition, the interlinking of industrial production with state-of-the-art communication and information technology is at the forefront, with data security being the top priority. The central advancement in comparison to Computer Integrated Manufacturing (Industry 3.0) is the use of Internet technologies to enable communication between machines, people and products. To allow this new technical standards and norms must be developed. The goal is to merge IT- and production technologies in order to make new innovative products and services possible. Thereby the efficiency of time, costs and quality shall be increased while the flexibility, adaptability and robustness of small and medium-sized enterprises (SMEs) shall be improved as well. As a result, Industry 4.0 is not only the core issue of the Digital Agenda of the Federal Government of Germany but also deeply rooted in our products, systems and working methods. Like all aixzellent products, our 'Industry 4.0 solution for SMEs' is based on the highest possible security standards and may contribute to the optimisation of your individual company structures in many ways. We are happy to advise you and look forward to your personal inquiry!
We celebrate our five-year company anniversary – celebrate with us!
After the brand aixzellent had been registered successfully in the German trade mark register in the late summer of 2012, we published our first news article on our new website five years ago. Since then, we regularly report on news, trends, threats, questions and products around the IT area. As a managed hosting provider, our focus is on data protection, encryption and secure, cost-efficient solutions for small and medium-sized enterprises (SMEs).
As successful IT service, we bundle our knowledge, our passion and our experience for the consultancy of our customers and the design of tailor-made open source solutions. What distinguishes us from other well-known hosting providers is our effort to offer our customers the highest level of security AND individuality at affordable prices. At the same time, we protect your data and systems 24/7 and assist you with advice and active support whenever needed.
We warmly invite you to celebrate this joyful event with us and to continue to benefit from our services in the future. And yet, it is worth to be quick! Our exclusive anniversary offer will safe you the monthly costs for all starter- and premium solutions up to 31-03-18! In addition to that, we grant you a special reduction on the set-up fee (starter 19€* instead of 29€* & premium 49€* instead of 99€*) for the implementation and installation of your aixzellent solution. After the 24-month term, the contract may be terminated on a monthly basis.
You are not sure which solution suits you best or you still have questions? No problem, we will advise you without any commitment and free of charge! Please do not hesitate to contact us at any time. You can find an overview of our starter- and premium- solutions here. We thank you for your trust and loyalty and look forward to the next years of successful cooperation with you!
Informational self-determination – the concept of decentralisation as an alternative to powerful data gathering companies
Maintaining a complex social network if hardly no one uses it and recently revealed a tremendous security breach? For the technology giant Google this is no longer up for discussion. In ten months, in August next year, the plug will be pulled. Googles in-house social network is going to be shut down. Google+ users will still be able to download their stored data and transfer them to other platforms.
But what are the alternatives? A switch to Facebook or other data gathering companies, platforms that earn money with our data and – using the example of Facebook – cannot even guarantee safekeeping for it? The question should rather be if we would like to leave our data to private companies. Anyone who refuses to do so, anyone who would like to regain control and responsibility over their own data and counteract a cultural constriction, currently has only one concrete option: open-source based networks. The data can be stored at home on your own computer or at a trusted provider. The advantages are obvious: Control of a video, for example, is completely retained – it can be removed at any time. And anyone who wants can even control who is allowed to see it. This of course applies to all types of data – texts, information and photos.
We present you two alternatives that set an uncommercial concept against the authoritarian-organized social networks.
Since 2010 diaspora* has offered its users the option to set up local servers anywhere in the world or to join existing servers. Decentralization is the keyword here – however it is still possible to connect seamlessly with the global community. In addition, the network offers its users the freedom to modify the source code and thus the possibilities of use and to adapt it to their own use. Just like the profile itself. Creativity can be given free rein, the real identity does not have to be used. The data are also not used to make money by evaluating interaction and advertising based on it, only for the possibility of global networking and user interaction. The user can specifically allow who can see posts and who cannot. As a result of individual privacy control, it is up to the user how private or public his profile may be. Even if your own contacts are not yet represented on diaspora*, your own account can be linked to other social networks and an extensive network can take place. More information about diaspora* is available at https://diasporafoundation.org/.
Mastodon is also an open source network that exists since 2016. As with diaspora*, there is no central server here, but a multitude of private ones, which are merged into a large network. Similar to Twitter, there is a limit of 500 characters for texts. Again, the user comes to the fore, there is no collection of data, no commercial use. A little insight and further information can be found at https://mastodon.social/about.
Curious? There are currently 23 projects at https://the-federation.info/, including diaspora* and mastodon, which are based on decentralized open-source software. Nodes connect these individual projects, allowing them to communicate with each other. Anyone who wants to reinvent and shape their right to informal self-determination has to be right here.
Environmental protection by aixzellent
Environmental protection is one of the most important and current challenges of our time. That’s why we implemented those criteria’s into our corporate philosophy a long time ago.
 As a company we are aware of our responsibility and therefore focus on sustainable solutions, such as the sensitization of our employees: The sensitization helps us to identify potentials for savings of energy and resources in our company, in the administration, for our business trips and even for our daily way to work. This is implemented and lived by our employees. By video conferencing, switching to public transport or establishing bicycles instead of cars we can reduce a significant amount of our companie’s CO2 emissions.
As a company we are aware of our responsibility and therefore focus on sustainable solutions, such as the sensitization of our employees: The sensitization helps us to identify potentials for savings of energy and resources in our company, in the administration, for our business trips and even for our daily way to work. This is implemented and lived by our employees. By video conferencing, switching to public transport or establishing bicycles instead of cars we can reduce a significant amount of our companie’s CO2 emissions.
 We also want to promote the energy-efficient use of the Internet. By running our servers exclusively in Germany at the provider Hetzner, we make sure that they are operated with 100% carbon dioxide-free and environmentally friendly hydropower. When selecting hardware or network components we use power consumption as essential criteria. If possible, we rely on the reuse of already manufactured server hardware and avoid energy-consuming and resource-consuming new productions.
We also want to promote the energy-efficient use of the Internet. By running our servers exclusively in Germany at the provider Hetzner, we make sure that they are operated with 100% carbon dioxide-free and environmentally friendly hydropower. When selecting hardware or network components we use power consumption as essential criteria. If possible, we rely on the reuse of already manufactured server hardware and avoid energy-consuming and resource-consuming new productions.
More information about our climate-neutral servers can be found here: https://www.hetzner.de/unternehmen/umweltschutz/
Digital policy and the recurring state trojans
In the future, intelligence services will be allowed to use malware to spy on suspects cell phones. This is not a new idea. According to Seehofer, the "draft of a law for the adaptation of the constitutional protection law" is supposed to be an overdue step in the fight against terrorists and right-wing extremists. For years, attempts have been made to legalize such action under the term "state trojan". But authorities tend to fail mostly because of themselves.
The pattern that the Ministry of the Interior uses is well known: A comprehensible purpose - the security of society - is supposed to justify this invasive intervention. But this does not only harm those it is aimed at. And the fact that the very Ministry of the Interior, which vehemently rejects a study on racism in the police force in order to pursue right-wing extremist structures in the public service, clearly shows that there are actually quite different interests at play here.
The proposed approach
Messaging services such as Signal, Threema and WhatsApp transmit their data in encrypted form. If malicious software is installed on the source of the communication, i.e. the cell phone, PC or tablet, the communication can be read by this software. The installation could then be disguised as a software update. Persons who are generally under suspicion or suspected of a crime should in this way be able to be spied on digitally. The crazy thing about it: Telecommunication providers (such as Telekom) are supposed to support the authorities by obliging them to smuggle in the spy software.
Data protection concerns
For years, various authorities have been trying to expand the scope of action for investigating authorities. So far, the Federal Court has created strict guidelines for digital surveillance, but since 2017 the police have had considerable leeway.1 And for years, data protectionists have also been warning that such trojans are technically illusory. A sharp distinction between ongoing communication - the actual target of the investigations - and the rest of the data is not possible. The verdict is also problematic in other respects:
The verdict is dominated by an idea of information technology systems that refers to concrete technical devices, social networks, e-mail providers and the cloud. But targeted systems with IP addresses are not only limited to laptops or cell phones: It could be cars, power plants, emergency call pillars or pacemakers. This means that not only could the most personal items be tapped, but that there could actually be danger to life and limb if such systems were infiltrated.2
In addition, the vulnerabilities that the software exploits to be installed on the device make it also more vulnerable to other attacks. It should be the government's intention to close these vulnerabilities.
The draft can be read here (german version): https://www.bmi.bund.de/SharedDocs/gesetzgebungsverfahren/DE/Downloads/referentenentwuerfe/anpassung-des-verfassungsschutzrechts.html
--------------------
1 Vgl. https://www.zeit.de/digital/datenschutz/2020-10/ueberwachung-geheimdienste-datensschutz-warnung-staatstrojaner-bundesregierung-schadsoftware/komplettansicht
2 https://www.ccc.de/de/updates/2016/staatstrojaner-bka
11/2015 - Let’s Encrypt with SSL-Certificates free of charge for everyone will start soon
As of December 3rd 2015, the Certificate Authority (CA) will initiate the Public Beta Phase of the tool Let’s Encrypt, offering complimentary SSL-Certificates which are then classified by the web browsers as being trustworthy. The protocol and the client are both based on Open Source solutions. The configuration of the server will become easier than ever before with the help of this tool: Let’s Encrypt just has to be started on your computer to issue such a certificate and to teach your server SSL. The tool contacts the CA in order to request for an SSL-Certificate of a specific domain. As soon as the CA has the proof that the server is really operating via the domain (domain validation), the tool obtains the verified certificate and is even able to configure the server for SSL if requested. Behind Let’s Encrypt are well known names such as Mozilla, Cisco, the Electronic Frontier Foundation and Akamai which formed and participate in an Internet Security Research Group (ISRG). The aim of this group is to standardise encrypted https-connections and addresses in order to ensure the security of data on the Internet. In addition to that, the CA has developed a new protocol (ACME) which is able to issue validated certificates automatically. Nevertheless, the tool is still in progress. However, with the solutions provided by aixzellent you will already now receive a certificate as a standard feature with all our packages! Find out more about our solutions for Groupware, Private Cloud and Web Hosting! Please do not hesitate to contact us, we are happy to assist you! [Source: heise online]
11/2016 – aixzellent has finalised the complete conversion from Zarafa to Kopano
Since mid 2016, we have been supporting the new Kopano groupware server software and have now finalised the complete migration. Needless to say we will continue to provide support for solutions and licenses running on the basis of Zarafa already. You would also like to change to Kopano or are interested in one of our managed hosting solutions? Contact us – we will be happy to assist you with your transition. Kopano offers a completely new kind of communication experience! Enhanced features increase employee productivity, improve team collaboration and enable a more efficient organisation of your work as well as immediate information exchange. Thanks to the open-source character, you always have complete control over all your data which you can view and edit at anytime from anywhere. The modular architecture of Kopano provides the basis for easy scalability and allows an uncomplicated integration into existing infrastructures. The replication of Microsoft Exchange Server functions insures a particularly easy and similar handling for users of Outlook or other suitable clients. Based on Z-push Kopano continues to support mobile devices while the ActiveSync protocol allows all your devices to receive push mails. For a comparison between the different Kopano clients, detailed information about the content as well as an overview of the functionality and performance of our Kopano solutions, please refer to our detailed product description. There you will also find additional information about the major changes in comparison to the previous solution.
Our new video for the campaign "More Internet Security" is available now!
Just in time with our anniversary and on the occasion of the transition from Zarafa to Kopano, we have updated our video for the campaign "More Internet Security" and are pleased to present the result here. Based on DANE (DNS-based Authentication of Named Entities) and DNSSEC (Domain Name System Security Extensions) protocols, aixzellent has developed various solutions to secure your data in the best possible way. The protocols use origin authentication to ensure that no invisible third party (man-in-the-middle) can engage in, intercept, or even steal data. On the one hand, especially small and medium-sized enterprises (SMEs) are often faced with a major challenge due to the lack of resources and know-how. On the other hand, data loss can be very expensive, particularly for SMEs, with far-reaching consequences that can even threaten their very existence. In addition to that, the dangers of increasing digitisation are steadily increasing in frequency and refinement. Therefore, we made offering tailor-made solutions for such companies at affordable prices with first-class service our business. An overview of our offer can be found here. What is special about each of our solutions is that they are designed specifically for you based on what you need. In that way we can guarantee the highest level of individuality and that you will only get and pay for what you really need. In a personal conversation we take the time to advise you free of charge and without any obligation. Please do not hesitate to contact us.
Judgment of the ECJ on (tracking) cookies
At the beginning of October, the European Court of Justice (ECJ) passed a significant judgment on cookie information obligations of website operators, which we would like to inform you about in this news.
Cookies and similar tracking methods may no longer be used unless customers have previously given their consent. The only exception is the operation of technically necessary cookies such as cookies for the login or the shopping cart. According to the court, website owners must now provide detailed information on the collection of cookies on their pages. The usual cookie notes (cookie banners) do not fulfill the requirements of the ECJ for three reasons:
- Users cannot really agree.
- These notes do not clarify anything about the data transfer and data usage in detail.
- Bare information banners don’t interrupt the automatic data transmission until the consent of the users. But that’s necessary to implement the privacy policy.
The judgment is important for everyone who is using cookies in the area of tracking or marketing on their website. It is also important for everyone who has included a Facebook like button or any similar button of social networks (Twitter, Instagram, LinkedIn etc.) on their pages.
The ECJ has also commented on four important issues:
- Website owners are always responsible for privacy violations, along with Facebook and other social networks.
- The unsolicited transmission of user data through the buttons of social networks on websites violates the data protection law.
- Competition associations may charge a fee for websites which have implemented the Facebook like button without consent.
- Cookies which are set up for tracking or advertising purposes must have a real consent of the website visitors. A cookie hint banner is not suitable for this purpose.
The ruling now can also be interpreted as an announcement to the German legislator to readjust German law to the EU rules. It is very likely that this will be closely aligned with the legal requirements of the ECJ.
We would like to point out to you that we are not allowed to offer legal advice. For further information we recommend the following page of the European Commission: https://wikis.ec.europa.eu/display/WEBGUIDE/04.+Cookies
ONLYOFFICE - Working without Microsoft and Google
We are pleased that we are now official partners of ONLYOFFICE, because as an open source solution it offers freedom and security in document collaboration and it is a real alternative to products from Microsoft and Google. In addition to collaboration via cloud storage, working with locally stored files is also possible. Besides web editors, ONLYOFFICE also scores with locally installable versions for Windows, macOS and Linux.
Developed in Latvia, the open source software includes editors for texts, tables and presentations, online document editors, a platform for document and project management, a CRM system and an e-mail client. The Community Edition for the server and the desktop editor are available free of charge. In addition, there are variants with more functions that can be used additionally as a cloud service. Another plus point: Since last year ONLYOFFICE is official partner of Nextcloud - in the current Nextcloud version ONLYOFFICE is directly part of the installation scope.
Deep integration with Nextcloud enables your users to collaborate with team members on Office documents in real time. It is possible to edit documents alone, with other users or with others who participate via a publicly shared link. Full support for MS Office formats such as DOCX and PPTX is provided as well as import and export of the Open Document format. Besides a modern and familiar user interface, ONLYOFFICE scores with the same browser and device independent document display, desktop level editing functions, public read-only/read-write links, the functions to track changes, accept/reject changes, multiple co-editing modes, commenting functions, mail merge and other benefits.
Since ONLYOFFICE does not require any external cloud storage for the collaboration of several users, it differs from Google and Microsoft in important points. A component that can be installed on self-hosted servers allows users full data sovereignty and meets the highest standards in data protection and data security. Integration into existing IT systems is possible without any problems.
Konzeption und Realisierung für das simTD Feldversuchslogging erfolgreich fertiggestellt
Im Auftrag von Hessen Mobil wurde erfolgreich eine Web-Smartphone-Applikation in nur 2 Monaten zur Logdateiverwaltung und -replikation konzeptioniert und realisiert. Die Verwaltung und Replikation der Logdateien des größten deutschen Feldversuchs in Sachen C2C/C2X (Car to Car/Car to Infrastructure) - simTD (Sichere Intelligente Mobilität) konnte so weitestgehend automatisiert und in die Prozesse von Hessen Mobil integriert werden. Es wird bis zum Ende des Feldversuchs mit bis zu 30 TB Datenvolumen in bis zu 10 Mio. Logdateien gerechnet.
12/2013 - Optimaler Betrieb auf dedizierten Systemen
In 2013 konnten wir unsere Kunden erneut von der Leistungsfähigkeit der Services von aixzellent in Sachen Cloud Computing und Managed Hosting überzeugen.
Auf Basis des Leistungsstarken Open Source Dokumenten Management Systems der Alfresco Software, Inc. sowie unserer Anpassungen für das Projektmanagement können Sie wichtige Projekte für den Zugriff großer Projektteams sicher bereitstellen, ohne sich um die Komplexität von Anwendung und Betrieb kümmern zu müssen.
Ergänzt um die Vorzüge der Open Source Groupware der Zarafa BV bleiben Sie in direktem Kontakt mit Ihren Mitarbeitern und Kunden. Darüber hinaus synchronisieren sich alle Ihre Geräte, egal ob Notebook, Tablet oder Smartphone automatisch und stets aktuell.
aixzellent supports the demand for digital fundamental rights in the EU
Facing the increasing globalisation some committed citizens of the European Union have developed a draft for a European DigitalCharta with the clear demand for digital fundamental rights. Within 14 months this has resulted in a comprehensive proposal for the ‘Charta der digitalen Grundrechte der Europäischen Unionʼ which was recently handed over to the EU Parliament in Brussels and is open to the public for discussion. It is devoted to the changes and new challenges of the digital world which inevitably affect the democratic fundamental rights of each and every EU citizen. In order to ensure freedom, justice and solidarity in the EU the shaping of this increasing digitalisation must be recognized and implemented as a European task. aixzellent is aware of this responsibility and supports this initiative with the utmost conviction about its correctness, necessity and the fact that the active participation of citizens in the EU we want to live in is of crucial importance. Please find the official website here. The draft of the European Digital Charter is originally written and published in German but an English-, French- and Spanish version are also available online. Click here to download the English version. There you will also find more information on the initiators, the background and frequently asked questions. In addition, you are welcome to participate actively in an open discussion and to check out the latest news and updates. Lastly, you have the opportunity to sign the DigitalCharta and thereby also support the need for such a charter as well as for the discussion about its further and future development. Over the past few days more than 1000 EU citizens who are also concerned about the design of the digital world have already signed the support list. After you have registered you will receive a confirmation mail. When you click the link in it, your name and function are publicly displayed. Your e-mail address will neither be published nor used in any other way. Therefore, take this opportunity to intervene and actively participate in shaping our future!
2018 will be all about IT security and the implementation of the EU GDPR
According to the latest report IT security and privacy 2017 of the National Initiative for Information and Internet Security (‘Nationale Initiative für Informations- und Internet-Sicherheit e.V.’ NIFIS), protecting and securing data is and will remain the most important issue for the German economy. As a result, the sensitivity to this topic will continue to grow inexorably. For the report, 100 executives and specialists from the IT industry were interviewed and their results evaluated.
Multiple answers were possible to assess the trends of the future. 95 percent of the respondents believe that increasing awareness will determine 2018. 94 percent of them see the protection against hacker attacks as trend-setting. The implementation of the EU General Data Protection Regulation (GDPR) will determine the next year according to 92 percent of the respondents.
Many of the data protection principles and concepts of the GDPR largely correspond to the previously valid EU data protection directive 95/46/EC. Their regulations were implemented in Germany with the German Federal Data Protection Act (‘Bundesdatenschutzgesetz’ BDSG). The provisions of the BDSG for companies are largely replaced by the provisions of the GDPR.
Since the new provision is an EU law, it is directly valid in all Member States and does not have to be implemented at the national level. Following the transitional period settled on 25 May 2016, the EU GDPR will apply two years after its entry into force, so that it will apply to everyone as of 25 May 2018. As a result, developers, programmers and above all software architects will have to rethink security and privacy by design.
[Sources: http://www.nifis.de/uploads/media/NIFIS-PI1612AD-Trends-2017-Datenschutz.pdf, https://www.finanzen.net/nachricht/aktien/trendstudie-2018-steht-ganz-im-zeichen-der-it-sicherheit-5790188, http://www.nifis.de/veroeffentlichungen/news/article/studie-ausg/ – further information: https://dsgvo-gesetz.de/]
XRechnung – Herausforderungen und Chancen
Die elektronische Rechnung wird ab dem 1. Januar 2025 zur Pflicht – und das für alle Unternehmen, die Rechnungen im B2B-Bereich stellen. Die XRechnung ist hier ein möglicher Standard. Doch was bedeutet das konkret, warum könnte es gerade für kleine Unternehmen eine Herausforderung sein, und wie können Sie diese bewältigen? Wir erklären die wichtigsten Punkte und stellen Ihnen eine Lösung vor, mit der Sie diese Umstellung stressfrei meistern.
Was ist die XRechnung?
Die XRechnung ist ein Standard für elektronische Rechnungen, der in der EU entwickelt wurde und speziell für den Austausch mit öffentlichen Auftraggebern vorgesehen ist. Sie basiert auf strukturierten Datenformaten (XML) und stellt sicher, dass Rechnungsdaten einheitlich, präzise und maschinenlesbar sind. Ziel ist es, den Rechnungsprozess effizienter und transparenter zu gestalten.

Was ändert sich?
Ab dem 1. Januar 2025 gilt die Pflicht zur elektronischen Rechnung in Deutschland für alle Unternehmen, die Rechnungen im B2B-Bereich stellen – unabhängig von ihrer Größe. Das bedeutet, dass auch kleine Betriebe und Freiberufler, die beispielsweise Dienstleistungen für Kommunen oder den Bund erbringen, ihre Rechnungen in diesem Format ausstellen müssen.
Herausforderungen für KMU
Während große Unternehmen oft bereits über ERP-Systeme verfügen, die den XRechnungs-Standard unterstützen, stehen viele kleinere Betriebe vor verschiedenen Herausforderungen:
-
Technischer Aufwand: Die Erstellung einer XRechnung erfordert spezialisierte Software oder Schnittstellen.
-
Kosten: Viele Anbieter setzen auf kostenpflichtige Lösungen, die für kleine Unternehmen unverhältnismäßig teuer sind.
-
Komplexität: Das Verständnis für die technischen Anforderungen ist oft begrenzt, was zu Fehlern oder Verzögerungen führen kann.
-
Vendor Lock-ins: Ein besonderes Risiko ist der sogenannte Vendor Lock-in. Viele Anbieter binden ihre Kunden an proprietäre Lösungen, was die Flexibilität einschränkt und die Kosten langfristig erhöht. Unternehmen sollten daher auf offene, skalierbare und unabhängige Lösungen setzen.
Unsere Lösung für Sie
Wir wissen, dass die Umstellung auf die XRechnung für viele Unternehmen eine Herausforderung darstellt. Deshalb haben wir eine einfache und kostengünstige Lösung entwickelt, die Ihnen folgende Vorteile bietet:
-
Benutzerfreundlichkeit: Unsere Plattform ist intuitiv und ohne IT-Vorkenntnisse nutzbar.
-
Flexibilität: Sie bleibt anbieterunabhängig und passt sich Ihren individuellen Bedürfnissen an.
-
Kosteneffizienz: Transparente Preise ohne versteckte Kosten.
-
Schnelle Integration: Starten Sie innerhalb weniger Stunden mit der Erstellung von XRechnungen.
Fazit
Die Pflicht elektronische Rechnungen zu stellen ab 2025 mag auf den ersten Blick kompliziert erscheinen, bietet aber auch Chancen, Prozesse zu modernisieren und langfristig Zeit sowie Kosten zu sparen. Mit der richtigen Lösung an Ihrer Seite wird die Umstellung zum Kinderspiel – sprechen Sie uns an und erfahren Sie, wie wir Sie unterstützen können!
The Confluence software by Atlassian enables you to discuss and process projects with your team effectively. You can create notes of meetings online and design product requirements or background articles with the active and direct participation of your entire team! Moreover, you have the possibility to discuss your projects by commenting directly on every Confluence page. Moreover, you can centralise all information of your different e-mail boxes and apps in one place! Giving each team, project and section a separate area will enhance the efficiency of your work. Thereby, Confluence does not only create order, but also has all your contents ready at your disposal anytime!
aixzellent hosts your Confluence data exclusively on servers in Germany. Our top priority is always to ensure the highest possible security for your projects and data. With aixzellent, you will always have the latest project management solutions available without having to bear expensive IT costs. Have we piqued your interest? We are looking forward to a personal contact for an individual consultation!
GitLab is a web application which may be used to manage various versions of software projects based on git. It provides you with unlimited public and private areas to add employees to your projects, multiple bug tracking and management functions, as well as a system to integrate your versions continuously (GitLab CI). With GitLab, you can also easily import your projects from GitHub, Bitbucket, GitLab.com, Gitorious.org, Google Code, Fogbugz, and any other Git repository via URL.
The GitLab Enterprise Edition (EE) is also equipped with additional functions which are particularly relevant for businesses and companies. One feature of the aixzellent premium version for SMEs is our exclusive support service, which guarantees support within 24 hours. In addition to that, the aixzellent GitLab premium version we host includes the exclusive option to store your data on servers in Germany so that we are able to guarantee the highest possible security standards.
Do not hesitate and take advantage of the opportunity not having to run your software projects on American servers. We will be glad to explain you all the different possibilities which our aixzellent GitLab packages offer you! Please contact us for personal advice!
Redmine is a flexible SW configuration-, version- and project management web application which is open source and written on the basis of Ruby on Rails. The software is independent from data and platforms and supports the management of various projects, their subcategories, users, and individual activities, which can all be accessed easily and flexibly.
Additionally, you have the possibility to unblock specific tasks for certain participants so that you will always keep control over all activities. You may create and edit reports, diagrams, mails, documents and calendars, or make use of project wikis and discussion forums for your own applications. The built-in time tracking system allows any configuration of the workflow and is based on freely selectable issue- and status types. Redmine runs with MySQL, PostgreSQL or SQLite and is already available in more than 34 languages.
We host your Redmine projects exclusively on servers located in Germany. aixzellent does not only stand for the highest possible security standards for your data, but also for the latest project management solutions, which we offer you always at low IT costs. Take advantage of our wide range of services tailored to your individual needs and contact us for a personal consultation!
Industry 4.0
Industry 4.0 is the name of the future project for comprehensive digitization of industrial production. There, the Internet plays the central role of the new technology, which aims to enable intelligent networking of machines and processes in industry with the help of information and communication technologies. The aim is to optimize not just one production step, but the entire value chain – a largely self-organized production should be possible. Uniform standards for different sectors of industry as well as the legal framework, changes in education and work, IT security and data protection pose new and particular challenges.
In this context, various opportunities open up for companies to benefit from intelligent networking. Optimized logistics, customer-centered solutions, flexible production and a convertible factory, a resource-efficient circular economy and the targeted use of data create new opportunities for employees and employers.
aixzellent-manufactory 4.0
We at aixzellent not only see the potential of the fourth industrial revolution, but want to play an active role in shaping it with our manufactory for sovereign IT solutions. Our individual solutions can:
- Digitally network your production,
- optimize utilization during production,
- improve the productivity and profitability of your company,
- bring companies closer to their customers,
- optimize the flow of goods,
- revise business models,
- ect.
In order to implement this, we find and implement solutions for smooth process integration in your specific business processes, such as a suitable online shop integration, which optimizes your sales processing in the network.
We also analyze the possibilities to actively control your processes in order to optimize the automation of your processes. Our specialists own the know-how to implement your ideas prototypically first and then permanently. For our cost-saving fast prototyping approach, we appreciate the almost unlimited application possibilities of the single-board computer Rasberry Pi: The small universal computer can not only be used as a remote-controlled multimedia station, weather station, room monitoring system, central irrigation controller or to monitor the network traffic. It also offers a reasonably priced basis for hardware prototypes with a wide range of applications, due to its open hardware and software platform and its diverse interfaces. There are hardly no applications that cannot be realized with the small computer.
Special protection for Critical Infrastructures in times of war
The topic of cybersecurity is gaining renewed importance, especially in the context of the Ukraine war. Critical Infrastructures are particularly important areas that need to be protected. Attacks on these can be very expensive, so it is worth investing in protecting them even in times of peace. The following blog post takes a closer look at the topic of Critical Infrastructures and highlights current problems.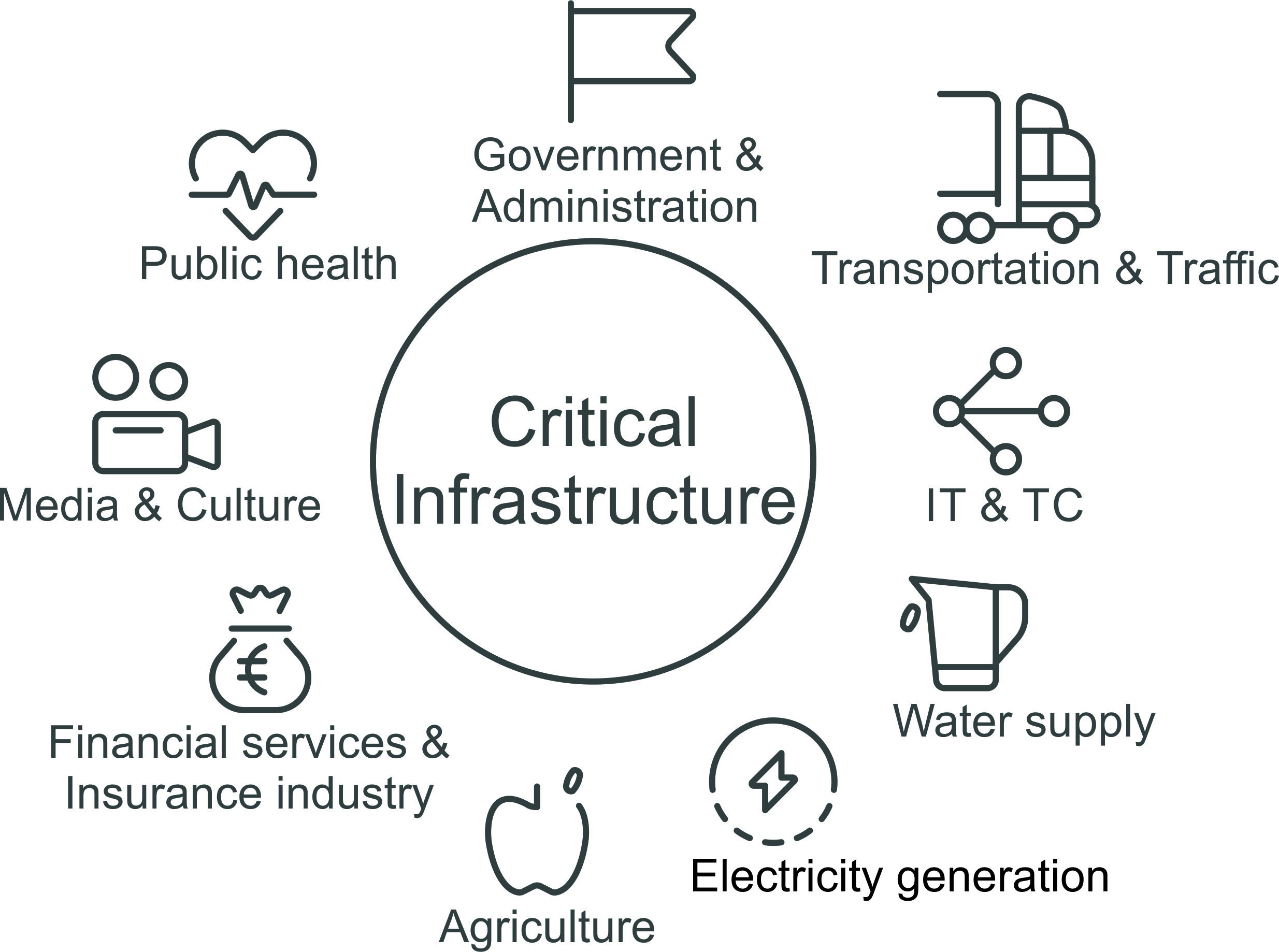
Critical Infrastructures are organizations or facilities with significant importance to the state community. For example, energy and water supply, transportation, as well as medical care and telecommunications fall under Critical Infrastructure. All of these provide us with essentials such as water, electricity and food. They form the basis of life, without which society would not function. The BBK (Federal Office of Civil Protection and Disaster Assistance) is responsible for protection, and its goal is to ensure that the population is supplied as well as possible.
Critical Infrastrucutres in times of war
In addition to global challenges such as climate change, the current Ukraine war poses a major problem for Critical Infrastructures due to the negative changes in the field of international security. In addition to terrorist attacks, there are threats that originate from cyberspace. For example, hacker attacks on the power grid can paralyze the power supply over a large area. In addition, growing digitization increases the interdependence between the Critical Infrastructures, which leads to an even larger attack surface. This makes it all the more important to protect the Critical Infrastructures from attacks by strengthening cybersecurity, primarily through the state.
The main problem with protective measures
The main problem with protecting Critical Infrastructures is that the law on mandatory IT security measures only covers cities with more than 500,000 inhabitants. Cities like Aachen, Augsburg, Münster and many others could be without water, electricity and food in case of cyber attacks on Critical Infrastructure. Thus, the protections are primarily beneficial to large cities; all smaller cities are not necessarily protected from the dangers of cyberattacks on supply chains by this loophole.
Is investing in IT protection worth it on a cost level?
Investments in IT protection are of considerable importance because the consequences of an attack on the Critical Infrastructures also entail fatal cost consequences. In the Anhalt-Bitterfeld district, for example, hackers broke into computers belonging to the authorities' IT systems, allowing secret data to be spied out and manipulated. The ransom demand amounted to a substantial € 500,000. 160 specialized procedures were affected and were not fully functional for about 1 year. Thus, the lack of IT protection ended up costing over € 2 million, the payment of which could have been avoided by prior investment in IT protection.
As digitization continues to grow, the increasing demands on the security of processes and systems must also be recognized and implemented. This makes it all the more important to prepare in times of peace for hacker attacks during a wartime event and take measures to protect against them.
aixCMS is written on the basis of Ruby on Rails and the content management system on which our own website is based. The application is particularly flexible and can be customised and tailored according to your personal requirements! With the elegant integrated editing capabilities enables you to change all contents easily and quickly – even without prior HTML knowledge! If you think that traditional content management systems are too complicated, our aixCMS is the right product for you! To support your authors and designers in their workings and to increase the efficiency of your web applications, any function which is unnecessary for your needs will be removed. Similarly, it is easy to add features you need. Therefore, this easy-to-use and appealingly designed system will please you and your employees!
Our experienced team develops our aixCMS constantly further – always following the spirit of the time-being. The software supports responsive designs by default, thereby providing you and your customers with the best support for all mobile platforms – from smartphones to tablets. In addition, it supports the highest possible security standards and transmits your data exclusively via an encrypted SSL/TLS connection. In future, you will ensure the highest standards and the optimal ranking of your website. In addition to that, we host your data exclusively on servers in Germany and do not require our own IT. Thereby, you can effectively manage your company with only a few employees at low costs. We are convinced that you are well advised with our CMS! Do you have any questions or would you like to know how we can design your individual content management system? Please do not hesitate and contact us directly for a personal consultation!
WordPress is a free web application for the creation and management of websites (images & texts) and web blogs. With the help of design templates, you can easily and quickly create individually customised designs with just one mouse click. Based on the program language PHP, WordPress requires a MySQL database. WordPress is also available as an application for the operating systems of various mobile devices (iOS, Android, Windows Phone, Blackberry OS, Symbian, HP webOS).
Our WordPress Managed Hosting is a service specifically designed on the basis of WordPress to maintain your contents. This also includes regular, comprehensive and automatic updates of the software and the operating system, as well as virus- and spam filters. In addition to an entire daily backup of the server, all available designs and plug-ins for advanced features are preinstalled. On request, we can also create your complete website according to your ideas.
We place particular emphasis on security and data protection according to German standards. Your data will only be transmitted via encrypted SSL connections and stored in German data centres, so that we can consistently guarantee security at the highest possible level and without human resources for your company. You can start right away to design your own web presence – easily, flexibly, quickly and individually. We would be glad to advise you personally, please feel free to contact us!
Contact
aixzellent
Theis Consult GmbH
Leonhardstraße 23-27
D - 52064 Aachen
Tel.: +49-241-60523-88
Fax.: +49 (0)241 46368007
E-Mail: sales@aixzellent.de
Our office hours are Monday to Friday from 08:00 am to 06:00 pm.
Statement on facebook
facebook is the largest global social network and is used enthusiastically by more than 1.5 billion people to share and communicate with friends all over the world. The use of the portal is free of charge but you have to accept certain conditions regarding privacy policies and the general terms (GTC). This is exactly the crucial point. Those who take the trouble to go through these documents will be confronted with a huge number of unclear and vague guidelines.
According to the currently applicable GTC (as of 30/01/2015) each user has to grant a permit for a worldwide license ‘explicitly’. This allows the corporation to use all contents (texts, pictures and videos) which are posted on facebook and protected by intellectual property rights. Moreover, for all contents which have been shared with others this IP-license does not even expire when you delete your account (Article 2.1).
This means in practice that the right of property and security of every post, every picture, every video, and anything else you publish on your facebook profile must always be handed over to and shared with third parties. As a consequence, the data and IP content are still yours but you have to allow facebook to collect and use them (Article 1). In this regard the possibility to change the privacy settings in order to determine what to share and with whom is also not very helpful. In case you really want to keep the control of your property you can basically not share anything with anyone anymore. However, then both the meaning and the benefits facebook is supposed to offer become increasingly questionable.
In addition to that, the information on data protection offer insights in what kind of data facebook collects, for which purpose and with whom it shares them. This concerns for instance the registration, all posts which are created and even messages. Moreover, facebook collects data on where a posted picture was taken, when a document was created, with whom you interact, which contents you look at, how often you do this, etc. This includes also all information others share about you.
Furthermore, all kinds of devices (computer, tablet, smartphone, etc.) you access facebook and use its services with, as well as other websites which are visited, are affected by this ‘information collecting mania’. Besides, facebook cooperates with third party companies for advertising and analysis purposes to which it transfers the collected data and information, even to the United States. In the end of 2015, the European Court of Justice (ECJ) clearly condemned the transfer of data to the US to be invalid. Also, the German consumer advice centre declared 19 provisions of the user conditions to be against the law and filed a suit against the corporation.
It is likewise complicated to file a lawsuit against facebook as private person. It is in principle possible under certain conditions but much more difficult in comparison to other companies. Legally tricky is the fact that facebook is not active in Germany. As a consequence, the court in California (USA) or the European headquarter of the United Group in Ireland are principally responsible. Finally, the enforcement of a judgment in these countries is very difficult.
The most recent developments concerning facebook are by no means less worrying. At the f8 Facebook Developers Conference the owner of the company Mark Zuckerberg presented his idea of a future universal platform. It is an attempt to additionally control all contents of sites outside facebook, while developing a network that the users are not supposed to leave anymore. A network, in which guidelines which are as unclear and vague as the general terms and the privacy policies decide what contents are feasible and legitimate.
The bottom line is that facebook is simply not a transparent platform. Not the user and his interests are in the foreground, but rather the benefits for facebook and the owner of the platform. All laws for the protection of personal data will be ineffective if they are constantly ignored by Internet companies. For all these reasons, we have as a company deliberately chosen not to be represented on facebook. However, since we support the basic idea of online networking you can find us on other, more user-friendly, platforms. As IT organisation focusing on data protection an security we would therefore also like to call special attention to alternative open source solutions.
One example in this regard is the diaspora* project: Instead of storing data on large centralised servers, which are part of a large organisation and are located in regions with questionable privacy policies, local servers (pods) can be set up anywhere in the world. You only need a diaspora-ID and may then decide yourself in which pod you want to register. Thereby you will always retain the rights over your data. We also support a pod under www.diasporaix.de. Of course, you may opt for any other server (Pod Liste, Pod Statistiken) like for instance the largest diaspora* pod geraspora or several other alternatives from which you can choose your pod yourself (wiki.diasporafoundation.org).
Finally, we would like to commend everyone to consider carefully what information to provide to whom, how, when, where and to be aware of all consequences.
For more information see:
Facebook:
Allgemeine Geschäftsbedingungen
Zusatz für Nutzer mit Wohnsitz in Deutschland
Datenrichtlinie
Press:
heise online - Zuckerbergs Vision von der Universalplattform
Spiegel Online - Verbraucherzentralen verklagen Facebook
Google Analytics not permitted in Europe from a data protection perspective
Google Analytics is used by 50-80% of all websites and is therefore one of the leading web analysis tools worldwide. However, the data quality could be improved, commercially and above all legally not unobjectionable. Now the integration of Google Analytics on EU websites has been officially declared as not allowed from a data protection perspective.
Google Analytics is a tracking tool used for traffic analysis of websites. Since the Internet is characterized by many indicators that provide information about user behavior, many website operators like to use the tool. With it, it is possible to analyze and optimize digital content of one's website in order to better reach one's target audience and thus generate more value for the company.
Austria's ruling by the authorities as a signpost for other countries .jpg)
Recently, the Austrian Data Protection Authority (DPA) officially stated that the use of Google Analytics violates the General Data Protection Regulation (GDPR). In addition to Austria, there are other countries where similar lawsuits are being initiated and implemented. In the Netherlands, there are already warnings that Google Analytics is likely to be banned soon, and in France even a tougher decision than in Austria has been made.
The decision in Austria is considered a landmark ruling that will serve as a model for similar cases. Even though the ruling only relates to netdoktor.at, it serves as a basis for other websites that use Google Analytics.
Why is Google Analytics not compliant with data protection?
One problem is the transmission of tracking data by Google Analytics to the USA, which is ultimately read by security authorities such as the NSA, which violates informational self-determination. Google itself has not (yet) commented specifically on the rulings.
What are the consequences of the ban for companies that use Google Analytics?
There are basically two possibilities as to how things will continue with Google Analytics. If the USA introduces adequate data protection in its country, EU citizens can be better protected. However, it is uncertain whether this will happen at all. Another option would be for US providers not to process data from abroad in the US. Consequently, a separation of products for the US and EU is not out of the question.
Data protection is close to our hearts
In the longer term, however, transparency and data economy play a crucial role in our society. A longer-term solution for website operators would be to use data-saving tools and only use tracking when it is really needed. We have already written about consent-free tracking with Matomo as an alternative to Google Analytics. As an open-source web analytics platform, Matomo, formerly Piwik, is a real alternative to Google Analytics and with the right use, website owners can even avoid using cookie banners.
As a company, we attach great importance to data protection and offer our customers various products that guarantee data protection. In addition, we will be happy to advise you on all aspects of this topic. We look forward to your contact request!
We support the new Zimbra groupware server software for Linux and have now completed the full transition to the new successor. Naturally, we continue to provide support for solutions and licences already based on Zarafa or Kopano. We would also be happy to assist you with switching to Zimbra.
Experience a whole new dimension of collaboration with the new Zimbra groupware! Zimbra combines modern email communication, calendars, task management and collaboration tools in one powerful, web-based platform. Thanks to its intuitive user interface, extensive integration options and high scalability, you can increase your employees' productivity and optimise internal communication within your company.
Detailed information about the new features, the various Zimbra clients and an overview of the performance and expandability of our Zimbra solutions can be found here.
The main changes compared to previous groupware solutions lie in improved web and mobile integration: Zimbra uses open standards such as IMAP, CalDAV, CardDAV and ActiveSync to ensure seamless synchronisation with common email and calendar applications. This allows you to benefit from smooth communication on all devices – whether desktop, notebook, smartphone or tablet.
All data you entrust us with are hosted exclusively in German data centres and only transmitted with secure SSL certificates. This way, we can guarantee security at the highest possible level and without human resources for your company. We would be pleased to advise you personally and design a solution based on your individual requirements! Do not hesitate to contact us, we are always at your deposal and looking forward to your ideas and suggestions!
We recommend Zimbra Professional Edition, which includes comprehensive support, Outlook for Windows (ZCO), mobile synchronisation, and archiving and search functions in addition to licences. Zimbra Standard Edition is available as a flexible, community-based option – ideal for test and development environments or smaller organisations with their own administration resources.
We offer you our support in running your own private e-mail server. You only have to activate your starter package with up to 50 mailboxes on this server. Subsequently you will be able to act on your own responsibility. We manage the entire set up of the server for you, back it up with anti-virus- and anti-spam software, update it regularly and are always there to help and assist you.
As a starter package, we recommend our “e-mail server in the box” solution. Based on open-source tools, this solution provides many features for you: Z-Push allows you for instance to access your mails, documents, contacts and appointments anywhere and from any device leke for instance from the desktop, tablet or smartphone. You can also use SMTP, IMAP or a web interface for the transfer.
All data you entrust to us with are hosted exclusively in German data centres and transmitted with domain validated SSL certificates encrypted. In this way, we can guarantee the highest level of protection, with the best possible security standards and without human resources. We would be pleased to advise you personally and design a solution based on your individual ideas! Please feel free to contact us, we are looking forward to your ideas and suggestions!
Matrix is an open, decentralized communication protocol for chat, IP, and video telephony. It enables cross-platform, end-to-end encrypted communication that remains completely under your control. Unlike proprietary messengers, with your own Matrix server, you retain complete control over all messages and files.
The open architecture allows you to use various Matrix clients—both existing open-source clients and individually developed solutions. This allows you to flexibly adapt usage to the requirements of your company.
On request, we can operate your own Matrix server in Germany—encrypted via SSL/TLS and strictly compliant with data protection regulations, of course.
Mattermost is a messaging platform for secure and efficient corporate communication over web, computers and phones. The web based team chat software is a real open source alternative to Slack, because it fulfills ambitious data protection and security standards. It offers all the functions that Slack users are familiar with: public and private chat rooms, one-to-one messaging, file exchange, user-defined emojis, webhooks, slash commands and multilingual support. It is also possible, among other things, to invite external employees or customers and to host company-wide workflows. Furthermore, SSO (single sign-on), extended authorizations, multi-factor authentication, performance monitoring, compliance reporting, custom branding and company search are among the special company functions.
The program, which is under the MIT license, is available for different platforms. It uses either MySQL or PostgreSQL as the database backend. As an aixzellent solution we host your server in Germany and your data is only transmitted via an encrypted SSL / TLS connection. We help you with commissioning, the productive integration of Mattermost into your environment and regular security updates.
Which service is right for me?
The web-based messaging solutions element and Mattermost score with cross-platform availability. You have your own desktop clients as well as clients for mobile operating systems. Direct messages, group messages, archives and data transmission are available in both applications.
We would be happy to advise you personally and work with you to design your own individual solution. Feel free to contact us!
Imprint
Responsible according to § 5 TMG (this information is required under German law):
Theis Consult GmbH
aixzellent
Oppenhoffallee 9-15
D - 52066 Aachen
Tel.: +49-241-60523-88
Fax.: +49 (0)241 46368007
E-Mail: webmaster@aixzellent.de
Managing Director (CEO):
Dipl.-Ing. Christian Roszak
Entry in the commercial trade register:
Register court: District court Aachen
Register number: HRB 14296
Sales tax ID according to § 27a sales tax law:
UST ID DE255535825
Legal disclaimer:
We check and update the information provided on our websites continuously. Nevertheless, an amendment or falsification of the data cannot be ruled out completely. Hence, no liability or guarantee regarding the actuality, correctness and completeness of the provided information can be assumed. The same applies to websites which are referred to via hyperlinks. aixzellent is not responsible for the contents of websites which are accessed through such links.
Gender-neutral formulation:
For the sake of a simplified language and a better readability the naming of different genders is renounced. However, we clearly distance ourselves from gender-specific discrimination, including in linguistic contexts, and would therefore like to point out that the predominant use of the male form should be explicitly understood as gender-independent.
Sources:
Confluence Logo - © Atlassian B.V. - design.atlassian.com/how-we-design/resources/
GitLab Logo - © GitLab B.V. - design by Ty Wilkins - about.gitlab.com/press/
Kopano Logo - © Kopano GmbH - https://kopano.com/press-materials/
Nextcloud Logo - © Nextcloud GmbH - nextcloud.com/press/
Redmine Logo - © Martin Herr - www.redmine.org/projects/redmine/wiki/Logo
Zarafa Logo - © Zarafa B.V. - www.zarafa.com
Zulip Logo - © Kandra Labs - https://zulipchat.com/
Kopano Video Meetings Logo - © Kopano GmbH - https://kopano.com/press-materials/
Mikogo Logo - © Snapview GmbH - www.mikogo.de
All trademarks are property of their respective owners. Other product or company names mentioned may be trademarks or trade names of their respective owner.
Bauarbeiter und Geschäftsfrau halten Daumen hoch - © Robert Kneschke - Fotolia.com
Information Technology Concept - © Nmedia - Fotolia.com
Männlicher Rücken mit dem Röntgenbild der Wirbelsäule - © ag visuell - Fotolia.com
Business people group working with laptop - © Kurhan - Fotolia.com
Old vintage file documents in storage room - © picsfive - Fotolia.com
Baustelle mit Kran - © Jakob Kamender - Fotolia.com
3D Aufkleber Rot Aktionspreis - © styleuneed - Fotolia.com
Orange flat icons - © Alex White - Fotolia.com
Professional young team or group of doctors - © Syda Productions - Fotolia.com
We are currently looking for new members to join our team
Training as an IT specialist (m/f/d) specializing in application development
Not interested in studying (anymore)?
Join us and become an IT specialist (m/f/d)
Are programming languages and databases your passion?
Are you creative, a team player, ambitious, and want to put your knowledge directly into practice?
Then you've come to the right place!
We develop customized high-end solutions for small and medium-sized businesses.
Our motto is always “Nothing is impossible!”
We are looking for committed, open-minded young people (m/f/d) in the field of application development to join our young and motivated team on October 1, 2025 (or earlier if possible).
We offer varied and exciting work on projects ranging from planning and implementation to user training and documentation.
We offer:
- Excellent chances of permanent employment
- Professional development and gaining experience
- Modern office space and state-of-the-art IT infrastructure
Our team spirit:
We embody team spirit, maintain open communication with an informal culture, and are committed to diversity in practice.
Your responsibilities:
- You will work independently in direct contact with customers, implementing individual business processes and solving any problems that arise conscientiously and in a goal-oriented manner.
- You develop, maintain, and test software using various programming languages and developer tools.
Your profile:
- At least a secondary school diploma; college dropouts (business informatics or computer science) are also welcome
- Basic knowledge in the field of IT
- Knowledge of programming languages is an advantage (e.g., JavaScript, HTML, and CSS, PHP, CMS, WordPress, or Ruby on Rails).
- Passion for IT & digitalization and technical affinity
- Analytical and logical thinking skills, as well as enjoyment in solving complex problems
- Organized and structured approach to work, as well as a high degree of initiative and willingness to learn
aixzellent is an emerging branch of Theis Consult GmbH, based on the experience of a successful engineering company. That way, we are able to draw on the experience gained over many years, and to expand our team directed towards IT- and App-solutions.
Current job offers:
The detailed job descriptions are only available in German.
Did we spark your interest?
Apply right now and send your complete application documents together with your desired salary via mail to jobs@aixzellent.de
Mastodon - An alternative to Twitter
Elon Musk is soon to take over Twitter and is already talking about changes to the social media platform. Concerns are being voiced by many critics. At the moment, however, the takeover cannot go ahead because Musk wants to have confirmed that spam accounts really make up less than 5% of the user base. Additionally, Musk wants to push the purchase price (as of May 18, 2022). Since a Twitter takeover is associated with many negative effects, alternatives such as Mastodon should be relied upon. In the following, we introduce Mastodon.
The name for the social media platform goes back to the American mastodon, a prehistoric relative of the mammoth. The Mastodon platform is a distributed microblogging service, was developed by German programmer Eugen Rochko in 2016, and gained considerable importance, especially recently.
Functionality and features
Mastodon is very similar to Twitter: messages are posted in public, where the group of people can be limited. The recipients can reply to the messages or forward them, which is called "boosting". When posting, it is also possible to embed links, graphics, audio and video files without any problems. The messages are not called a tweet, but a toot. These can be given an expiration date so that deletion is automated. In addition, there are hashtags and the option to follow people. It is also possible to save messages as favorites. The user's own profile is very similar to that of Twitter, but liking is symbolized by an asterisk and referred to as favoriting. Mastodon can be accessed not only via the browser, but also via mobile operating systems.
Advantages over Twitter
The biggest advantage of the Twitter alternative is that it is organized in a decentralized manner. Thus, there is no "mastodon.com", but many servers cooperating with each other, which are called instances. If a communication is to take place on the same instance, an @ with the corresponding account name is sufficient. Otherwise the address of the instance is still appended. Mastodon can also be used to communicate with platforms in the Fediverse that support either the ActivityPub or OStatus protocol. Fediverse is based on Federated Universe and is composed of the word "federation" and "universe". It represents a network consisting of federated, interdependent social networks, microblogging services, and online publishing websites. The ActivityPub protocol is an open, decentralized social networking protocol. Content can thus be created, uploaded or deleted through the included client-to-server API. Another positive aspect is that no user tracking is used.
Mastodon provides users with significantly more characters than Twitter. Instead of 280 characters, there are 500, which significantly reduces the typing restriction.
Even if the overview takes some getting used to, it offers an enormous advantage: in contrast to Twitter, Mastodon has transparent rules and thus also timelines whose content is not shaped by an opaque algorithm. Mastodon offers users a simple and chronological overview. On the one hand there is the federated timeline, on the other hand the local timeline. The former shows all public messages from a given instance and the instances with which that instance exchanges. The latter always contains all public posts of the members of only one instance.
Distribution
In May 2017 there were only 650 000 Mastodon users, but within the next 5 years the social media platform grew significantly. There are now 5 million user (as of May 2022). The trend continues to rise, with Musk's Twitter takeover fueling the increased growth of Mastodon users.
In addition to celebrities, a great many companies use Mastodon, including us! The social media platform has many advantages and is an excellent Twitter alternative. Register with Mastodon and follow us!
Lorem ipsum dolor sit amet, consetetur sadipscing elitr, sed diam nonumy eirmod tempor invidunt ut labore et dolore magna aliquyam erat, sed diam voluptua. At vero eos et accusam et justo duo dolores et ea rebum. Stet clita kasd gubergren, no sea takimata sanctus est Lorem ipsum dolor sit amet. Lorem ipsum dolor sit amet, consetetur sadipscing elitr, sed diam nonumy eirmod tempor invidunt ut labore et dolore magna aliquyam erat, sed diam voluptua. At vero eos et accusam et justo duo dolores et ea rebum. Stet clita kasd gubergren, no sea takimata sanctus est Lorem ipsum dolor sit amet.
Lorem ipsum dolor sit amet, consetetur sadipscing elitr, sed diam nonumy eirmod tempor invidunt ut labore et dolore magna aliquyam erat, sed diam voluptua. At vero eos et accusam et justo duo dolores et ea rebum. Stet clita kasd gubergren, no sea takimata sanctus est Lorem ipsum dolor sit amet. Lorem ipsum dolor sit amet, consetetur sadipscing elitr, sed diam nonumy eirmod tempor invidunt ut labore et dolore magna aliquyam erat, sed diam voluptua. At vero eos et accusam et justo duo dolores et ea rebum. Stet clita kasd gubergren, no sea takimata sanctus est Lorem ipsum dolor sit amet.
HPC
Lorem ipsum dolor sit amet, consetetur sadipscing elitr, sed diam nonumy eirmod tempor invidunt ut labore et dolore magna aliquyam erat, sed diam voluptua. At vero eos et accusam et justo duo dolores et ea rebum. Stet clita kasd gubergren, no sea takimata sanctus est Lorem ipsum dolor sit amet. Lorem ipsum dolor sit amet, consetetur sadipscing elitr, sed diam nonumy eirmod tempor invidunt ut labore et dolore magna aliquyam erat, sed diam voluptua. At vero eos et accusam et justo duo dolores et ea rebum. Stet clita kasd gubergren, no sea takimata sanctus est Lorem ipsum dolor sit amet.
OTC
Lorem ipsum dolor sit amet, consetetur sadipscing elitr, sed diam nonumy eirmod tempor invidunt ut labore et dolore magna aliquyam erat, sed diam voluptua. At vero eos et accusam et justo duo dolores et ea rebum. Stet clita kasd gubergren, no sea takimata sanctus est Lorem ipsum dolor sit amet. Lorem ipsum dolor sit amet, consetetur sadipscing elitr, sed diam nonumy eirmod tempor invidunt ut labore et dolore magna aliquyam erat, sed diam voluptua. At vero eos et accusam et justo duo dolores et ea rebum. Stet clita kasd gubergren, no sea takimata sanctus est Lorem ipsum dolor sit amet.
Lorem ipsum dolor sit amet, consetetur sadipscing elitr, sed diam nonumy eirmod tempor invidunt ut labore et dolore magna aliquyam erat, sed diam voluptua. At vero eos et accusam et justo duo dolores et ea rebum. Stet clita kasd gubergren, no sea takimata sanctus est Lorem ipsum dolor sit amet. Lorem ipsum dolor sit amet, consetetur sadipscing elitr, sed diam nonumy eirmod tempor invidunt ut labore et dolore magna aliquyam erat, sed diam voluptua. At vero eos et accusam et justo duo dolores et ea rebum. Stet clita kasd gubergren, no sea takimata sanctus est Lorem ipsum dolor sit amet.
Lorem ipsum dolor sit amet, consetetur sadipscing elitr, sed diam nonumy eirmod tempor invidunt ut labore et dolore magna aliquyam erat, sed diam voluptua. At vero eos et accusam et justo duo dolores et ea rebum. Stet clita kasd gubergren, no sea takimata sanctus est Lorem ipsum dolor sit amet. Lorem ipsum dolor sit amet, consetetur sadipscing elitr, sed diam nonumy eirmod tempor invidunt ut labore et dolore magna aliquyam erat, sed diam voluptua. At vero eos et accusam et justo duo dolores et ea rebum. Stet clita kasd gubergren, no sea takimata sanctus est Lorem ipsum dolor sit amet.
Lorem ipsum dolor sit amet, consetetur sadipscing elitr, sed diam nonumy eirmod tempor invidunt ut labore et dolore magna aliquyam erat, sed diam voluptua. At vero eos et accusam et justo duo dolores et ea rebum. Stet clita kasd gubergren, no sea takimata sanctus est Lorem ipsum dolor sit amet. Lorem ipsum dolor sit amet, consetetur sadipscing elitr, sed diam nonumy eirmod tempor invidunt ut labore et dolore magna aliquyam erat, sed diam voluptua. At vero eos et accusam et justo duo dolores et ea rebum. Stet clita kasd gubergren, no sea takimata sanctus est Lorem ipsum dolor sit amet.
Lorem ipsum dolor sit amet, consetetur sadipscing elitr, sed diam nonumy eirmod tempor invidunt ut labore et dolore magna aliquyam erat, sed diam voluptua. At vero eos et accusam et justo duo dolores et ea rebum. Stet clita kasd gubergren, no sea takimata sanctus est Lorem ipsum dolor sit amet. Lorem ipsum dolor sit amet, consetetur sadipscing elitr, sed diam nonumy eirmod tempor invidunt ut labore et dolore magna aliquyam erat, sed diam voluptua. At vero eos et accusam et justo duo dolores et ea rebum. Stet clita kasd gubergren, no sea takimata sanctus est Lorem ipsum dolor sit amet.
Lorem ipsum dolor sit amet, consetetur sadipscing elitr, sed diam nonumy eirmod tempor invidunt ut labore et dolore magna aliquyam erat, sed diam voluptua. At vero eos et accusam et justo duo dolores et ea rebum. Stet clita kasd gubergren, no sea takimata sanctus est Lorem ipsum dolor sit amet. Lorem ipsum dolor sit amet, consetetur sadipscing elitr, sed diam nonumy eirmod tempor invidunt ut labore et dolore magna aliquyam erat, sed diam voluptua. At vero eos et accusam et justo duo dolores et ea rebum. Stet clita kasd gubergren, no sea takimata sanctus est Lorem ipsum dolor sit amet.
Lorem ipsum dolor sit amet, consetetur sadipscing elitr, sed diam nonumy eirmod tempor invidunt ut labore et dolore magna aliquyam erat, sed diam voluptua. At vero eos et accusam et justo duo dolores et ea rebum. Stet clita kasd gubergren, no sea takimata sanctus est Lorem ipsum dolor sit amet. Lorem ipsum dolor sit amet, consetetur sadipscing elitr, sed diam nonumy eirmod tempor invidunt ut labore et dolore magna aliquyam erat, sed diam voluptua. At vero eos et accusam et justo duo dolores et ea rebum. Stet clita kasd gubergren, no sea takimata sanctus est Lorem ipsum dolor sit amet.
Lorem ipsum dolor sit amet, consetetur sadipscing elitr, sed diam nonumy eirmod tempor invidunt ut labore et dolore magna aliquyam erat, sed diam voluptua. At vero eos et accusam et justo duo dolores et ea rebum. Stet clita kasd gubergren, no sea takimata sanctus est Lorem ipsum dolor sit amet. Lorem ipsum dolor sit amet, consetetur sadipscing elitr, sed diam nonumy eirmod tempor invidunt ut labore et dolore magna aliquyam erat, sed diam voluptua. At vero eos et accusam et justo duo dolores et ea rebum. Stet clita kasd gubergren, no sea takimata sanctus est Lorem ipsum dolor sit amet.
Lorem ipsum dolor sit amet, consetetur sadipscing elitr, sed diam nonumy eirmod tempor invidunt ut labore et dolore magna aliquyam erat, sed diam voluptua. At vero eos et accusam et justo duo dolores et ea rebum. Stet clita kasd gubergren, no sea takimata sanctus est Lorem ipsum dolor sit amet. Lorem ipsum dolor sit amet, consetetur sadipscing elitr, sed diam nonumy eirmod tempor invidunt ut labore et dolore magna aliquyam erat, sed diam voluptua. At vero eos et accusam et justo duo dolores et ea rebum. Stet clita kasd gubergren, no sea takimata sanctus est Lorem ipsum dolor sit amet.
Lorem ipsum dolor sit amet, consetetur sadipscing elitr, sed diam nonumy eirmod tempor invidunt ut labore et dolore magna aliquyam erat, sed diam voluptua. At vero eos et accusam et justo duo dolores et ea rebum. Stet clita kasd gubergren, no sea takimata sanctus est Lorem ipsum dolor sit amet. Lorem ipsum dolor sit amet, consetetur sadipscing elitr, sed diam nonumy eirmod tempor invidunt ut labore et dolore magna aliquyam erat, sed diam voluptua. At vero eos et accusam et justo duo dolores et ea rebum. Stet clita kasd gubergren, no sea takimata sanctus est Lorem ipsum dolor sit amet.
Lorem ipsum dolor sit amet, consetetur sadipscing elitr, sed diam nonumy eirmod tempor invidunt ut labore et dolore magna aliquyam erat, sed diam voluptua. At vero eos et accusam et justo duo dolores et ea rebum. Stet clita kasd gubergren, no sea takimata sanctus est Lorem ipsum dolor sit amet. Lorem ipsum dolor sit amet, consetetur sadipscing elitr, sed diam nonumy eirmod tempor invidunt ut labore et dolore magna aliquyam erat, sed diam voluptua. At vero eos et accusam et justo duo dolores et ea rebum. Stet clita kasd gubergren, no sea takimata sanctus est Lorem ipsum dolor sit amet.
Lorem ipsum dolor sit amet, consetetur sadipscing elitr, sed diam nonumy eirmod tempor invidunt ut labore et dolore magna aliquyam erat, sed diam voluptua. At vero eos et accusam et justo duo dolores et ea rebum. Stet clita kasd gubergren, no sea takimata sanctus est Lorem ipsum dolor sit amet. Lorem ipsum dolor sit amet, consetetur sadipscing elitr, sed diam nonumy eirmod tempor invidunt ut labore et dolore magna aliquyam erat, sed diam voluptua. At vero eos et accusam et justo duo dolores et ea rebum. Stet clita kasd gubergren, no sea takimata sanctus est Lorem ipsum dolor sit amet.
Lorem ipsum dolor sit amet, consetetur sadipscing elitr, sed diam nonumy eirmod tempor invidunt ut labore et dolore magna aliquyam erat, sed diam voluptua. At vero eos et accusam et justo duo dolores et ea rebum. Stet clita kasd gubergren, no sea takimata sanctus est Lorem ipsum dolor sit amet. Lorem ipsum dolor sit amet, consetetur sadipscing elitr, sed diam nonumy eirmod tempor invidunt ut labore et dolore magna aliquyam erat, sed diam voluptua. At vero eos et accusam et justo duo dolores et ea rebum. Stet clita kasd gubergren, no sea takimata sanctus est Lorem ipsum dolor sit amet.
Promotion of Open Source
In January 2001, the beginning of a success story was written: Jimmy Wales published the online encyclopedia Wikipedia, marking the beginning of open source development. Until today, however, the topic of open source has played a subordinate role in Germany and has been pushed into the background. However, open source brings with it many advantages that are currently not being exploited.
What is Open Source?
Open source refers to software or code that is freely accessible to the public. Thus, it can be viewed, modified or distributed by third parties. Often the open source software can be used for free or at a very low price.
How does it look with the use in Germany?
Unfortunately, Germany fares rather poorly compared to other countries. This is mainly because, although digital sovereignty has been created in recent years, nothing or little has been done by the state. There is neither a common policy in the area of open source nor is this a major topic in our society. However, the EU Commission recommends that every EU state promote open source at all levels and in all areas, as this has a significant positive impact on economic growth. In addition, open source has a good effect on other aspects as well, which we will explain below.
So why is open source so important?
For one thing, the skills and knowledge of workers in companies can be kept up-to-date and even expanded through open source. In addition, the employees are motivated by varied activities, which also increases the work productivity of each individual. Furthermore, software development skills are specifically promoted. Countries that already promote open source also have excellent software development skills, according to studies.
Secondly, the operating costs in the public sector would decrease. This is because the overall costs in the IT sector would decrease significantly, as proprietary software would be dispensed with in the public sector.
In addition, dependency on third-party vendors would greatly decrease and digital sovereignty would be strengthened. Furthermore, services such as standardization, knowledge transfer and community development can be provided through open source. Consequently, open source foundations play an essential role here.
Another benefit is the increase in start-up foundations. According to comprehensive studies, an increase of 10% in open source contributions would enable the creation of an additional 600 start-ups per year. This is mainly driven by the high quality of (free) open source software, which results from the collaboration of many people who have different skills. Thus, many young companies benefit from this, which then can more easily bring innovative products to the market.
We offer a wide range of Open Source
We as a company attach great importance to the use of open source. Therefore, it is also important to us to offer you the best possible open source offers. We provide you with a wide range of attractive offers, where we are happy to advise you. If you have any further questions or concerns, please feel free to contact us at any time.
.jpg)
The Managed Cloud & Hosting service we have developed is an ‘all-inclusive package’ aimed specifically at SMEs. Nevertheless, these are flexible, tailor-made solutions that are not offered by ‘traditional’ providers. With the help of automated provisioning and monitoring systems, we maintain and monitor your systems securely, efficiently and cost-effectively. All solutions are hosted exclusively in Germany.
Can't find the solution you're looking for? We would be happy to advise you personally and design a solution based on your individual requirements and ideas. Have we sparked your interest? Get in touch with us directly.
Privacy policy for the use of our website
The protection of your data is our (aixzellent, Oppenhoffallee 9-15, D - 52066 Aachen; responsible in terms of Art. 24 (1) EU-GDPR) highest priority. Due to this we would like to inform you in accordance with the German Telemedia Act (TMG), the latest version of the Federal Data Protection Act (BDSG new) and the EU Data Protection Regulation (EU-GDPR) about the purpose, nature and extent to which personal data are processed while visiting and using our website.
You can exercise your right to information as well as the right to correct, delete or restrict the processing of your data - insofar as this is permissible due to other existing legal obligations - at any time.
You have the option of contacting the data protection supervisory authority responsible for us with a complaint in connection with data processing.
When contacting us (e.g. by e-mail), the user's details are processed for the purpose of processing the enquiry and in the event that follow-up questions arise, in particular for the implementation of pre-contractual measures.
We would like to point out that data transmission over the Internet (e.g. communication by e-mail) can be subject to security gaps. A complete protection of the data against access by third parties is not possible.
Data collection when using this website
In order to minimise the extent to which personal data are collected and processed as much as possible, aixzellent refrains in accordance with the EU GDPR largely from collecting and storing personal data and completely from the use of external analysis tools such as Google Analytics. Hence, you can visit our website without providing any personal information. However, for operational reasons and safety-related analyses to avoid and evaluate any system errors and/or "cyberattacks" on our website, so-called "server logs" are, according to the legal basis for data processing in the EU GDPR, automatically stored in our system for a week. They include the IP address as well as the date and time of access. In addition to that, the browser type and -version, referrer URL, the names of requested web pages/files and the amount of sent data are transmitted. This information is not used for any other purpose and is completely deleted after seven days.
Usage of cookies (session cookies)
By using our website you accept the use of cookies. These are small text files which are archived on your computer and stored by your browser. They do neither damage your computer, nor contain viruses. They only serve to make our offer more user-friendly, more efficient and safer while enabling the use of certain functions, e.g. search function. These so-called session cookies are automatically deleted after your visit to our website. To be informed about the setting of cookies, you can adjust your browser accordingly. This way you can specify exactly which cookies you want to allow or disable. Moreover, you can enable the automatic deletion of cookies when closing the browser. Please note that disabling cookies may limit the functionality of our website.
Anonymised analysis of visitor flows
To analyse the behaviour of users visiting our website, we make use of the open source web tracking tool Piwik/Matomo. With this alternative to Google Analytics, the data used to follow up website visitors is only processed internally by us. This means that this data will not be forwarded to and used by any third party. Instead they are only stored on our own server and analysed exclusively by us. In this way, we can also guarantee that all data is saved without exception and solely on systems in Germany. For anonymisation, the last digits of the IP address (the last byte of the IPv4 address) are made illegible. A personal reference of the data is thereby reliably eliminated.
Changes to the privacy policy
We reserve the right to amend this privacy policy. The current privacy policy version for the use of our website is always accessible on our homepage and via https://www.aixzellent.com/en/privacy. Our customers will be informed in written if the privacy policy changes fundamentally.
Nextcloud is a new, free cloud server software based on owncloud version 9. In the addition to the extra features, it also has special business features (Premium). For example, multiple people (employees) can access and edit Microsoft Office files, PDF documents, images, etc. This makes the platform suitable for both private use and businesses. Of course, this excellent solution is also hosted in Germany and your data is transmitted exclusively via an encrypted SSL/TLS connection.
With the Sharing REST API, you can control and manage the sharing of your data from mobile apps or desktop clients. WebRTC conferencing and Spreed.ME support allow you to hold secure video conferences and exchange short messages via chat. Thanks to its open source nature, Nextcloud offers not only a high level of data security and flexibility, but also transparency and the opportunity for active participation. The software is regularly updated by us and is additionally protected by an anti-virus programme. We would be happy to advise you personally and work with you to design your own individual solution. Get in touch with us!
ONLYOFFICE's deep integration with Nextcloud allows your users to collaborate on Office documents with team members in real time. It is possible to edit documents alone, with other Nextcloud users, or with others who participate via a publicly shared link. Full support for MS Office formats such as DOCX and PPTX is provided, as well as import and export of the Open Document Format.
The advantages of ONLYOFFICE at a glance:
- A modern and familiar user interface,
- The same document display in every browser,
- Desktop-level editing functions,
- Public read-only/read-write links,
- Track changes, accept/reject changes,
- Multiple co-editing modes,
- Commenting,
- Mail merge
- etc.
- Use on your own servers, giving you full control over your data.
- 100% open source guarantees transparency and no vendor lock-in!
- Instead of passing data on to third parties, ONLYOFFICE runs in your own data centre, guaranteeing 100% document confidentiality.
We would be happy to advise you personally and work with you to design your own individual solution. Get in touch with us!
Who are our customers?
We are working with customers from all over Europe (e.g. Germany, France, Belgium, the Netherlands, Austria and Switzerland). Though, both big customers and public administrations are among our clients, our services are also explicitly aimed at small and medium-sized enterprises, e.g. craftsmen, engineers, architects, doctors, offices etc.
BigBlueButton
Organization of the digital conference of GfT e.V. incl. participant management, technical rehearsal, creation of user manuals, technical support & follow-up.
Web Hosting
ITS Germany is the German Association for intelligent transport systems. Our contribution consists of managing, running and maintaining the contents of the website.
Groupware / Web Hosting / Redesign / Relaunch
The 'Bioland' farm of the Gauchel family is located on the northern outskirts of Aachen. We look after the maintenance and management of their website and Groupware by Kopano.
Web Design / Web Hosting
We provide all neccessary services regarding the maintanance and contents of the website, and take care about managing and running it.
Groupware / Web Design / Web Hosting
We designed the website's logo and take care about maintaining and managing the website, as well as the Groupware by Kopano.
Web Design / Web Hosting
Since 1991 engaged in the consultation, design, announcement, and project supervision of intelligent transport systems (IVS/ITS).
Private Cloud / Web Hosting
Project management's conception based on Alfresco Software Inc. Establishment of DMS including adjustments according to customer's requirements. Management and operation of systems.
Managed Services
Conception and establishment of a dedicated server for operating Atlassian Confluence as collaboration platform for the TISA's working groups. Management and operation of systems.
Web Design / Web Hosting
AIAMO is a project funded by the Federal Ministry of Transport to develop AI-based environmental and mobility management. We are responsible for the web design and web hosting of the website.
Secure & DSGVO-compliant teamwork with Nextcloud
Nextcloud is a freely available software for storing data on your own server and the smart open source alternative for DSGVO-compliant teamwork. It can be accessed through various end devices and synchronization of server and clients is possible everywhere. Thanks to its open source character, Nextcloud offers a high level of data security and flexibility, as well as transparency and the possibility of active participation. But what about the use of Nextcloud in projects? The following entry provides an overview of the software's security.
Use in projects
From a project perspective, the content stored in the cloud is worth protecting in terms of information security. The corresponding compliance rules must be defined here. This can refer, for example, to the laws, rules and regulations contained in the BSI-Grundschutz. Furthermore, also to the DSGVO and export control regulations. These must be ensured in the corresponding Nextcloud instance for the project through configuration (e.g. 2FA etc.) and, if necessary, additional agreement with all project participants. We will be happy to advise you on the DSGVO-compliant use of Nextcloud in your projects.
How secure is Nextcloud?
Two exemplary uses confirm the security of Nextcloud in the following areas: First, based on a decision by the Informationstechnikzentrum Bund (ITZBund) in 2018, the software is used in ministries and other institutions by 300,000 employees throughout Germany. Secondly, since 2019, the software has been used by authorities in France, Sweden and the Netherlands for data exchange. In the future, 100,000 employees working in the French Ministry of the Interior will also use Nextcloud.
According to AGPLv3 (3rd version of GNU Affero General Public License), the software includes all components, which means that there is no export restriction that can be seriously controlled. This means that Nextcloud users are entitled to download the source code, even if the software is only run on a server as a service. Consequently, the software is not made available for direct download and therefore also represents a license for free software with copyleft.
How to get Nextcloud?
The software is available from all over the world, including from the websites https://download.nextcloud.com/server/releases/nextcloud-22.1.0.zip and https://github.com/nextcloud. However, it is time-consuming and requires IT know-how to set up the software on your own. To avoid mistakes, the installation should be done by professionals. We offer the possibility of complete setup and hosting on servers owned by the customers. Feel free to contact us! We are at your disposal for any questions and other concerns.

The Managed Cloud & Hosting service we have developed is an ‘all-inclusive package’ aimed specifically at SMEs. Nevertheless, these are flexible, tailor-made solutions that are not offered by ‘traditional’ providers. With the help of automated provisioning and monitoring systems, we maintain and monitor your systems securely, efficiently and cost-effectively. All solutions are hosted exclusively in Germany.
Can't find the solution you're looking for? We would be happy to advise you personally and design a solution based on your individual requirements and ideas. Have we sparked your interest? Get in touch with us directly.
Mattermost is a messaging platform for secure and efficient corporate communication over web, computers and phones. The web based team chat software is a real open source alternative to Slack, because it fulfills ambitious data protection and security standards. It offers all the functions that Slack users are familiar with: public and private chat rooms, one-to-one messaging, file exchange, user-defined emojis, webhooks, slash commands and multilingual support. It is also possible, among other things, to invite external employees or customers and to host company-wide workflows. Furthermore, SSO (single sign-on), extended authorizations, multi-factor authentication, performance monitoring, compliance reporting, custom branding and company search are among the special company functions.
The program, which is under the MIT license, is available for different platforms. It uses either MySQL or PostgreSQL as the database backend. As an aixzellent solution we host your server in Germany and your data is only transmitted via an encrypted SSL / TLS connection. We help you with commissioning, the productive integration of Mattermost into your environment and regular security updates.
element is a cross-platform open source software for chat, IP and video telephone using the matrix protocols. Existing communication platforms such as IRC, Slack, Twitter, Telegram and Apple iMessage are integrated. This large network means that cross-platform communication on multiple devices can be implemented without any problems. Group chats, the exchange of pictures and other files and sharing them is also possible. Riot also offers a searchable archive and can serve as a kind of collective memory in companies or organizations.
The messenger is also open source and supports optional end-to-end encryption. That distinguishes it from Mattermost. Messages can be encrypted with one click within the matrix network. At your request, we host our own matrix server in Germany – of course, exclusively via encrypted SSL / TLS connections.
Which service is right for me?
The web-based messaging solutions Mattermost, Riot and Zulip score with cross-platform availability. You have your own desktop clients as well as clients for mobile operating systems. Direct messages, group messages, archives and data transmission are available in all three applications. Riot also offers video and internet telephony. These functions have so far only been available to a limited extent with Mattermost and Zulip. Riot can also score with end-to-end encryption; the other two services have transport encryption.
We would be happy to advise you personally and work with you to design your own individual solution. Feel free to contact us!
Manufactory for sovereign IT solutions
We are a Manufactory for sovereign IT solutions meaning that we do not offer “ready-made solutions” but act exclusively based on your wishes, needs and requirements. Our competent and experienced team of experts coming from engineering, computer science, telecommunications and electrical engineering will take the time to develop your optimal solution jointly and individually with you in a personal conversation. Thereby, we rely on our motto: “Nothing is impossible!” As a service provider, our tailored high-end solutions are especially designed for small and medium enterprises (SME). Besides the highest possible level of data security, individual offers at fair prices with personal customer contacts are our key priorities and very close to our hearts. What is special is that you will only have to communicate your ideas to us, while we will take care of all configurations, services and the maintenance for you (Managed Hosting). Enterprise versions including special features are also available on request. Do not hesitate to contact our team of experts and take the chance to create your personal web presence more easily, quickly, flexibly, cheaply, securely and individually!
Who we are
With us you have a competent and experienced partner at your side. We are the company's successful range of information and communication technology, a leading consultant and planner for traffic installations, transport telematics and traffic management systems in Europe. We offer a comprehensive range of IT services.
What we can do for you
Drawing on years of experience and our interdisciplinary know-how, we design the optimal solution for your problem in cooperation with you, to realise it quickly and effectively subsequently. Thereby, we are happy to include commercial- as well as open source solutions.
Where we are
Originating from the successful engineering office Theis Consult (established in 1991), we are evolving to a Full Service Provider for our customers on the basis of our success. With our staff of engineers, communication engineers and computer scientists, as well as a network of experts from all relevant areas, we offer our customers all the necessary skills for an efficient order fulfilment.
The name of our service

is a combination of the German adjective "exzellent" (excellent) and the French name for Aachen "Aix-la-Chapelle" [ɛkslaʃapɛl].
For the definition of excellent the dictionary provides e.g. above-average, perfect , technically complete, extraordinary, remarkable, exceptional, special, teriffic, great, outstanding, glorious, admirable, exquisite, quality, irreplaceable, selected, first-class, high-grade, precious, very good, classy, phenomenal, exclusive, etc.
This name is our agenda and our daily challenge.
Environmental Protection by aixzellent
Environmental protection is one of the most important and current challenges of our time. That’s why we implemented those criteria’s into our corporate philosophy a long time ago.
 As a company we are aware of our responsibility and therefore focus on sustainable solutions, such as the sensitization of our employees: The sensitization helps us to identify potentials for savings of energy and resources in our company, in the administration, for our business trips and even for our daily way to work. This is implemented and lived by our employees. By video conferencing, switching to public transport or establishing bicycles instead of cars we can reduce a significant amount of our companie’s CO2 emissions.
As a company we are aware of our responsibility and therefore focus on sustainable solutions, such as the sensitization of our employees: The sensitization helps us to identify potentials for savings of energy and resources in our company, in the administration, for our business trips and even for our daily way to work. This is implemented and lived by our employees. By video conferencing, switching to public transport or establishing bicycles instead of cars we can reduce a significant amount of our companie’s CO2 emissions.
 We also want to promote the energy-efficient use of the Internet. By running our servers exclusively in Germany at the provider Hetzner, we make sure that they are operated with 100% carbon dioxide-free and environmentally friendly hydropower. When selecting hardware or network components we use power consumption as essential criteria. If possible, we rely on the reuse of already manufactured server hardware and avoid energy-consuming and resource-consuming new productions. In addition, we obtain 100% of our electricity from natural power.
We also want to promote the energy-efficient use of the Internet. By running our servers exclusively in Germany at the provider Hetzner, we make sure that they are operated with 100% carbon dioxide-free and environmentally friendly hydropower. When selecting hardware or network components we use power consumption as essential criteria. If possible, we rely on the reuse of already manufactured server hardware and avoid energy-consuming and resource-consuming new productions. In addition, we obtain 100% of our electricity from natural power.
More information about our climate-neutral servers can be found here: https://www.hetzner.de/unternehmen/umweltschutz/
Our aixCMS
We have been continuously developing our aixCMS since 2012. Recently, some new functions have found their way into our website builder again. It is now possible to create new and varied animations on the websites. In addition, the replacement of background images and the setting of jump marks in the navigation bar is now easily possible. We took this as an opportunity to present our CMS once again.
Written on the basis of Ruby on Rails, aixCMS is the content management system on which our own website is based. The application is particularly flexible and can be customized specifically according to the wishes of our customers. One of the reasons for this is that we can adapt the intuitive customer user interface (the CMS editor) to the customer's needs, thus avoiding operating errors and the need for time-consuming training. The layout is designed to be easy to use and attractive. Changes can be made by the customer without HTML knowledge. In order to support the authors and designers in their work and to increase the efficiency of the web applications, the functions that are superfluous for the customer are removed. On the other hand, it is possible to add more functions needed by our customers. For this we consult with the customer very well, so that the requirements are worked out precisely and the customer is very satisfied with the final result.
Security
Our aixCMS is constantly developed by our team and always follows the spirit of the times. It supports responsive designs by default and is thus perfectly adapted to any smartphones, tablets and laptops/PCs. In addition, aixCMS supports the highest possible security standards and transmits data exclusively via an encrypted SSL/TLS connection. As a result, the highest standards and optimal ranking of the website are guaranteed. Furthermore, we host the data exclusively on servers in Germany and do not require our own IT. In this way, our customers can effectively run their business with minimal staff effort.
Maybe another CMS after all?
We are convinced for many reasons that our customers are best advised with our CMS. Alternative CMS, such as TYPO3, certainly offer many great features. Nevertheless, on the one hand, it happens again and again in customer projects that the complexity in typical use rather leads to problems and higher expenses. On the other hand, the flexibility to implement individual designs quickly reaches the limits of the "standard functionality" of the corresponding tools. Plug-ins or individual extensions then come into question as the only "help", which is cumbersome and actually avoidable. If our customers nevertheless choose an alternative CMS, we are of course happy to advise them there as well. Many of our customers use Wordpress, for example.

This entry-level product is specifically designed for small and medium-sized businesses (SMBs) which require a simple Internet presence based on LAMP (Linux, Apache, MySQL, PHP), Ruby on Rails, or HTML. As with all aixzellent solutions, we attach great importance to security and data protection. All data you entrust us with are hosted exclusively in German data centres and only transmitted with secure SSL certificates. Thereby, we can guarantee protection for your company at the highest possible level, without human resources and at low IT costs.
The change or upgrade to another product is perfectly easy and possible at any time. We would be pleased to advise you personally and design a solution based on your individual necessities! Feel free to contact us, we are looking forward to your ideas and suggestions!
aixCMS is written on the basis of Ruby on Rails and the content management system on which our own website is based. The application is particularly flexible and can be customised and tailored according to your personal requirements! With the elegant integrated editing capabilities enables you to change all contents easily and quickly – even without prior HTML knowledge! If you think that traditional content management systems are too complicated, our aixCMS is the right product for you! To support your authors and designers in their workings and to increase the efficiency of your web applications, any function which is unnecessary for your needs will be removed. Similarly, it is easy to add features you need. Therefore, this easy-to-use and appealingly designed system will please you and your employees!
Our experienced team develops our aixCMS constantly further – always following the spirit of the time-being. The software supports responsive designs by default, thereby providing you and your customers with the best support for all mobile platforms – from smartphones to tablets. In addition, it supports the highest possible security standards and transmits your data exclusively via an encrypted SSL/TLS connection. In future, you will ensure the highest standards and the optimal ranking of your website. In addition to that, we host your data exclusively on servers in Germany and do not require our own IT. Thereby, you can effectively manage your company with only a few employees at low costs. We are convinced that you are well advised with our CMS! Do you have any questions or would you like to know how we can design your individual content management system? Please do not hesitate and contact us directly for a personal consultation!
WordPress is a free web application for the creation and management of websites (images & texts) and web blogs. With the help of design templates, you can easily and quickly create individually customised designs with just one mouse click. Based on the program language PHP, WordPress requires a MySQL database. WordPress is also available as an application for the operating systems of various mobile devices (iOS, Android, Windows Phone, Blackberry OS, Symbian, HP webOS).
Our WordPress Managed Hosting is a service specifically designed on the basis of WordPress to maintain your contents. This also includes regular, comprehensive and automatic updates of the software and the operating system, as well as virus- and spam filters. In addition to an entire daily backup of the server, all available designs and plug-ins for advanced features are preinstalled. On request, we can also create your complete website according to your ideas.
We place particular emphasis on security and data protection according to German standards. Your data will only be transmitted via encrypted SSL connections and stored in German data centres, so that we can consistently guarantee security at the highest possible level and without human resources for your company. You can start right away to design your own web presence – easily, flexibly, quickly and individually. We would be glad to advise you personally, please feel free to contact us!
With this tool training for users in real time at remote locations is possible. The web-based open source online learning tool supports the real time sharing of
- audio,
- video,
- foils,
- whiteboard,
- chat,
- screensharing
- etc.
Participants can also take part in the conferences with their webcams and invite guest speakers.
The simple API simplifies the integration of your own products and scores with a long list of existing integration options with applications from third-party providers such as Canvas, Drupal, Moodle, RedMine, Wordpress and much more. For example, BBB can be integrated into Moodle LMS so that users who have not taken part in a live session can view it later on demand.
We would be happy to advise you personally and work with you to design your own individual solution. Feel free to contact us!
The open source software enables video conferences with one or more participants. In addition to video or audio chat, Jitsi Meet also offers functions of desktop sharing and screen sharing of certain windows to present content. In addition, an integrated chat function is available to share text-based content with other participants. Furthermore, Jitsi Meet is also available as an app on Android and iOS.
On the basis of WebRTC, data or media streams are transmitted in encrypted form via datagram transport layer security and secure realtime transport protocol. At your request, we host your own Jitsi Meet instance on servers in Germany with your data protection always in focus.
We would be happy to advise you personally and work with you to design your own individual solution. Feel free to contact us!
We have been supporting Kopano clients for several years and have had the best experience with the open source collaboration software. However, the video conference tool Kopano Meet also works completely independently of other Kopano apps, so installation of other Kopano apps is not a mandatory requirement.
The software, which is independent of the client device, was developed for use in companies and allows "peer to peer" encrypted communication. It can easily be rolled out within a private cloud. The first version of Kopano Meet includes high-definition video and audio calls, one-to-one calls and group calls.
With us you can set up your own Kopano Meet instance! All data that you entrust to us is hosted exclusively in German data centers and transmitted with SSL certificates. In this way we can guarantee the highest level of security for your company without any human resources.
We would be happy to advise you personally and work with you to design your own individual solution. Feel free to contact us!
Mikogo enables you to display your own selected screen content on the Internet and thus make it accessible to other authenticated users. A 256-bit AES encryption enables remote control of the screen and file exchange among the individual participants in the respective session. After the necessary rights have been assigned, the presenter can take control of another computer and vice versa. With the integrated whiteboard function, the presenter can mark out screen contents or add comments. In addition, the sessions can be paused, recorded, blocked for participants arriving late and released again. A session planner that allows you to reserve session numbers for use over and over again can be helpful for regular product presentations or meetings.
Mikogo comes from a company based in Germany. This means that they are subject to German data protection regulations and also have their servers in Germany. At your request, aixzellent takes over the acquisition and setup of the software and the appropriate licenses (Professional and Enterprise) for the desired end devices. Our service also includes regular updates of the software.
We would be happy to advise you personally and work with you to design your own individual solution. Feel free to contact us!
Increase in cyberattacks
Many studies show that the number of companies affected by cyberattacks is always on the rise and an increase in cybercrime victims can also be assumed in the future.
In addition, cybercrime is coming even more into focus due to the Ukraine war. Many ransomware-attacks are carried out by Russian hacker groups. The target is not only Ukraine, but also other European countries.
The current situation is worsening
Cyberattacks are no longer singular cases. According to a study commissioned by the digital association Bitkom, 84% of the more than 1000 companies surveyed were affected at least once last year by data theft or sabotage, for example. The German economy alone suffered losses of around 203 billion euros. Alarming numbers that show how damaging such attacks are. In the worst case, critical infrastructures, administrations or supply chains are paralyzed, which can lead to problems of public safety and lack of supply. 2021 the Anhalt-Bitterfeld administration was attacked by ransomware, so that regular operations were not possible for months. This is considered to be the first cyber catastrophe case in Germany.
Digital war - the "Vulkan Files"
The so called "Vulkan files" now reveal, that Russia apparently wants to use the fatal consequences of an successful attack. They name important transport- or energy networks as targets. But being in control of the internet in occupied territories also plays a central role in the Russian cyberwar. Vulkan is said to be just one of over 30 competing Russian companies.
"These examples, as well as many incidents in recent years, make it clear that there is a real threat from cyberspace to Germany's critical infrastructure." Konstantin von Notz (Bündnis 90/Die Grünen) member of the Bundestag
Lack of security as the main problem
The main reason why many companies are affected by successful cyberattacks is a lack of investment in IT security. This is because the costs for appropriate measures are high and they do not pay off directly as long as no damage occurs. However, the consequences of an attack are even more expensive and additionally damage the company's reputation. Investments in IT security measures are therefore essential.
Preventing a hacker attack is a continuous process that pays off. The following graphic shows the procedure according to the BSI-Grundschutz standards.
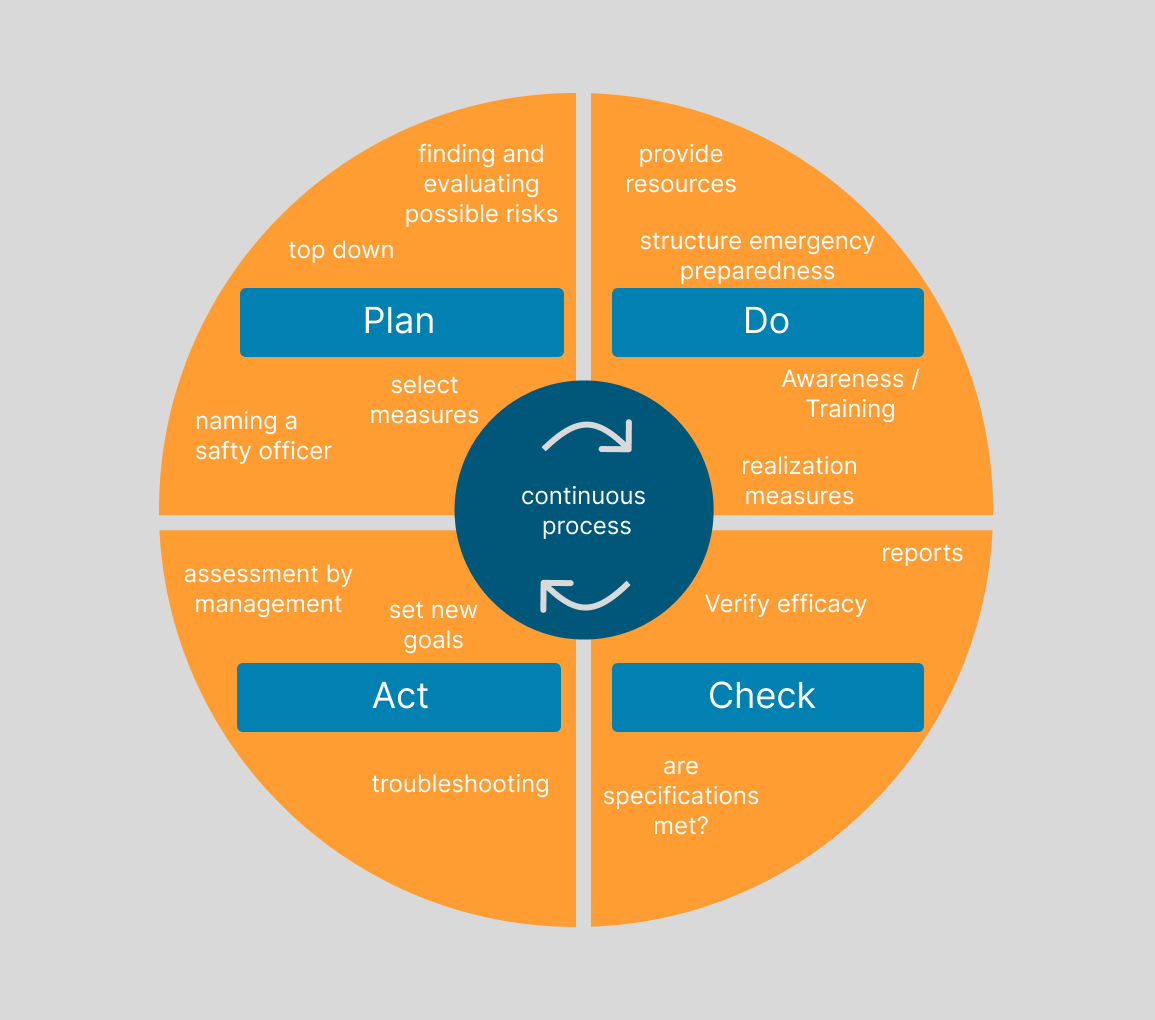
Our company pays attention to cybersecurity (security by design) from the very beginning of the solutions & services we offer. In addition, our customers' data is backed up daily and transmitted exclusively in encrypted form. The employees of our company who are responsible for IT security are certified as BSI basic protection practitioners and therefore have the necessary qualifications in data protection and IT system security. If you have any questions about our services, please contact us by e-mail or phone. We will be happy to advise you!









 customizable
customizable